Cyber guy. Used to be a lurker but I guess now I can be the occasional poster.
| Site | https://mattysplo.it |
| Pronouns | He/Him |
Cyber guy. Used to be a lurker but I guess now I can be the occasional poster.
| Site | https://mattysplo.it |
| Pronouns | He/Him |
And of course I ended up making my own - originally thinking I'd have to make stuff up, eventually I realized ATT&CK just kind of works for a taxonomy in itself if done cleanly enough. Sort of like biology, just 'Kingdom-Order-Phylum' what you see and it makes a bit more sense than what I tested.
To prove that point, I cross-walked a bunch of ATT&CK techniques against three big frameworks to show how they fail. Categories overlap, or don't apply to observed behavior. Not super scientific but demonstrates how those events can cluster and analyst has to just pick a label.
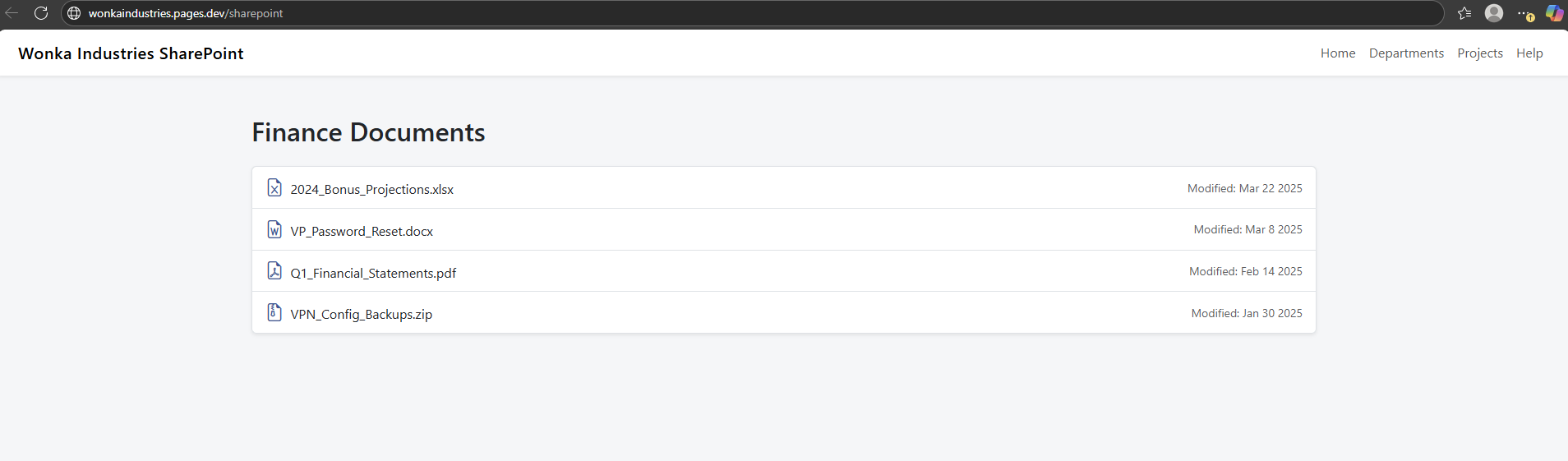
Each fake app in the dashboard points to a static HTML trap hosted on Azure Static Web Apps or Cloudflare Pages. Want a fake SharePoint? Clone the UI in 15 mins, add some fake docs. Fake VPN? No need to hang some open SSH bait out on the open, you just put the whole thing behind a tile.
No more junk telemetry from mass scans. Instead, you get signal-rich interactions from actors who made it through your fake login, picked a fake app, and thought they’d reached the crown jewels. All of this lives outside your real infra and adds that layer of initial access telemetry. Super handy.
This lets you simulate real identity flows—credential stuffing, MFA fatigue, password sprays—without touching production. You can even add basic login automation for realism, like scheduled logins or profile updates.
An IdP allows you to impersonate your real login screen and then the user dashboard enables some pretty sweet modular design. As big/expensive or small/cheap as you like. Mix in throwaway "real" services with static HTML clones. Deploy a T-Pot and call it your VPN. The attacker just sees tiles.