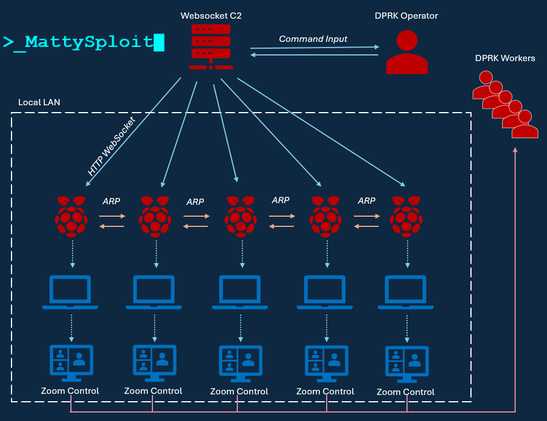
New from me: I've been lookin into ways to stand up a cloud-based honeynet that 1) didn't look like some random nub hangin out there on open internet, 2) was as cheap/fast as possible, 3) actually looked "real" and not such an obvious trap. I found that answer in using an external IdP like Okta
Seems like honeynet in cloud has 3 options, none of which I like: Put it in your tenant and segregate it, put it in another tenant named somethin different, or hang it out there on its own w/ no real identifiers at all. None are great, as you're either increasing risk or making it look less legit.🧵