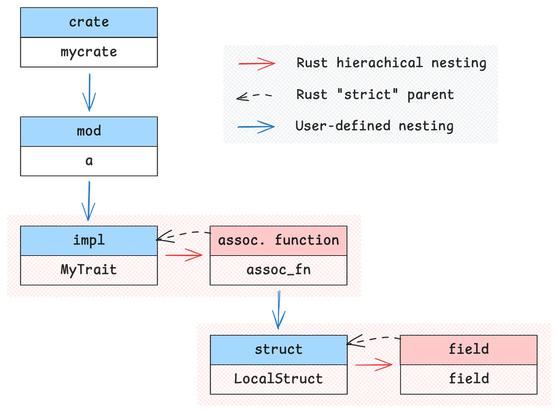
Thrilled to welcome @blement to Cryspen's Tools and Proofs team! 🎉 Clément's expertise in formal methods (PhD from Inria Paris!) will be for conducting rigorous proofs and enhancing our tooling. Welcome, Clément! 🚀
| Website | https://www.cryspen.com/ |
| Github | https://github.com/cryspen |