• Security research and open source at Datadog
🇨🇭🇫🇷
| Website | https://christophetd.fr |
| GitHub | https://github.com/christophetd |
| 🪦 |

| Website | https://christophetd.fr |
| GitHub | https://github.com/christophetd |
| 🪦 |
By making minor changes to command-line arguments, it is possible to bypass EDR/AV detections.
My research, comprising ~70 Windows executables, found that all of them were vulnerable to this, to varying degrees.
Here’s what I found and why it matters 👉 https://wietze.github.io/blog/bypassing-detections-with-command-line-obfuscation
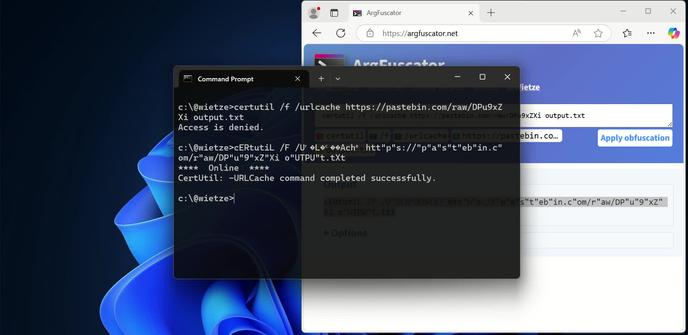
Defensive tools like AVs and EDRs rely on command-line arguments for detecting malicious activity. This post demonstrates how command-line obfuscation, a shell-independent technique that exploits executables’ parsing “flaws”, can bypass such detections. It also introduces ArgFuscator, a new tool that documents obfuscation opportunities and generates obfuscated command lines.
New research: We've been monitoring a threat actor publishing dozens of trojanized GitHub repositories targeting threat actors, leaking hundreds of thousands of credentials along the way
https://securitylabs.datadoghq.com/articles/mut-1244-targeting-offensive-actors/
This post describes an in-depth investigation by Datadog security researchers into a threat actor dubbed MUT-1244, which targets other malicious actors as well as security practitioners and academics.
Some interesting research by my colleague @christophetd on default service accounts in GCP. Looks at how default rights can be in place and some of the risks to GKE environments.
https://securitylabs.datadoghq.com/articles/google-cloud-default-service-accounts/
New blog post: A SaaS provider's guide to securely integrating with customers' AWS accounts
https://securitylabs.datadoghq.com/articles/securely-integrating-with-customers-aws-accounts/
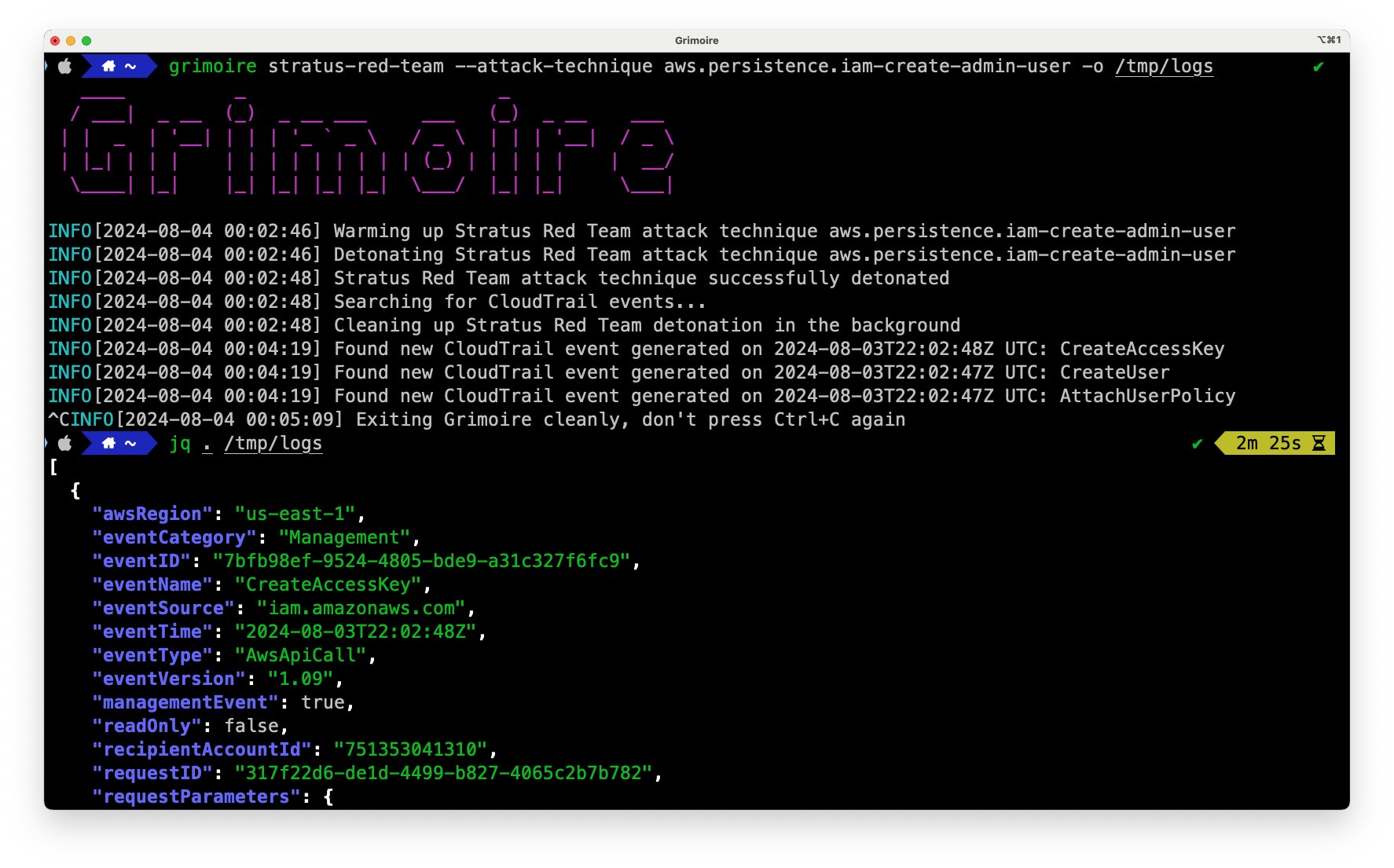
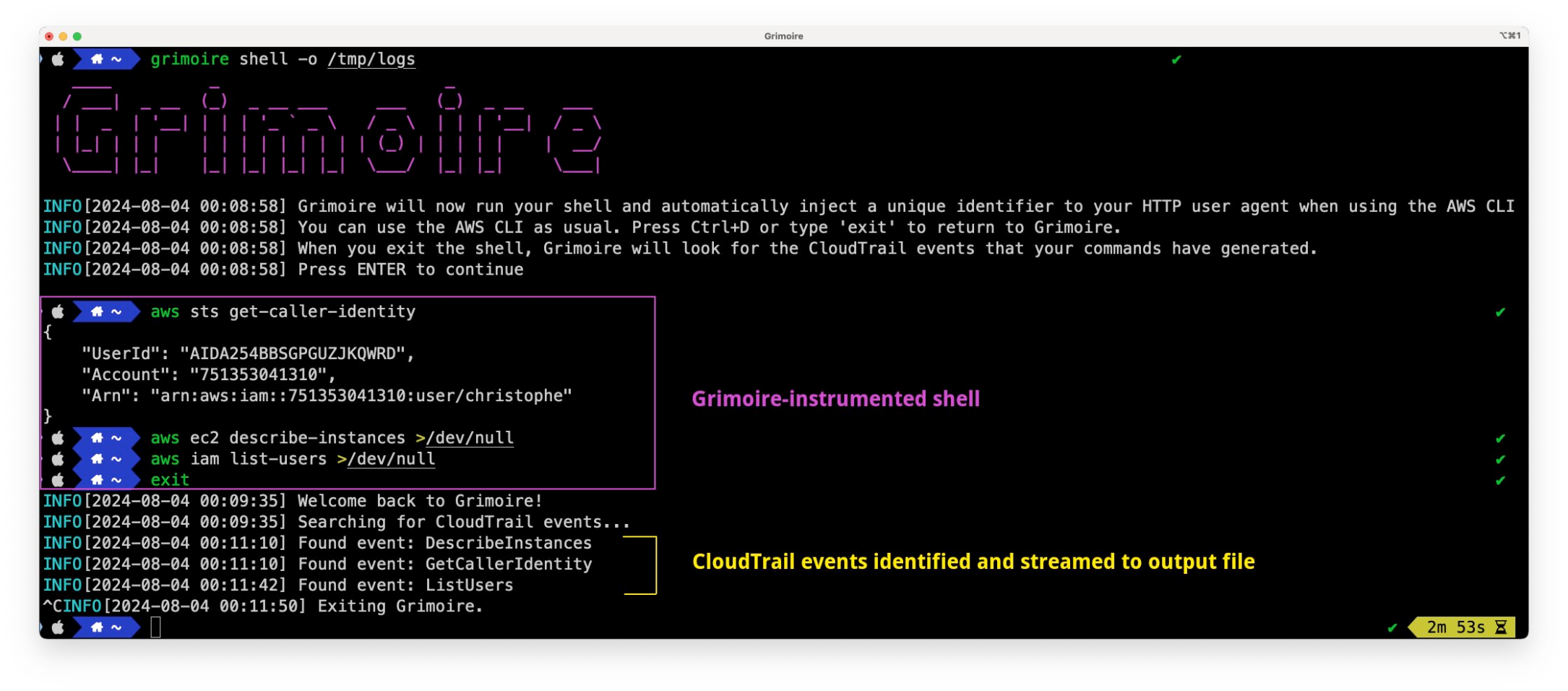
A little late on Mastodon, but I'm excited to release a new open-source tool to help with AWS detection engineering: Grimoire!
https://github.com/datadog/grimoire
https://securitylabs.datadoghq.com/articles/announcing-grimoire/
Stop worrying about 'allowPrivilegeEscalation' in Kubernetes
https://blog.christophetd.fr/stop-worrying-about-allowprivilegeescalation/
Super excited that my colleague Ian Ferguson (staff engineer in our Runtime Infrastructure team) is giving this talk at fwd:cloudsec next week.
Includes a brand new open-source project that facilitates multi-cloud IAM 👀
🛎️ DING! AWS Security Digest 157 is ready!
1️⃣ IMDSv2 enforcement: coming to a region near you! @christophetd
2️⃣ AWS Bulletin regarding CVE-2024-3094 (+ Interesting blogpost)
3️⃣ Amazon GuardDuty EC2 Runtime Monitoring is now generally available
Link below...
IMDSv2 enforcement: coming to a region near you!