| Gitlab | https://gitlab.com/Hack_Char |
| Blog | https://hack-char.dev |
Char
- 84 Followers
- 147 Following
- 1.1K Posts
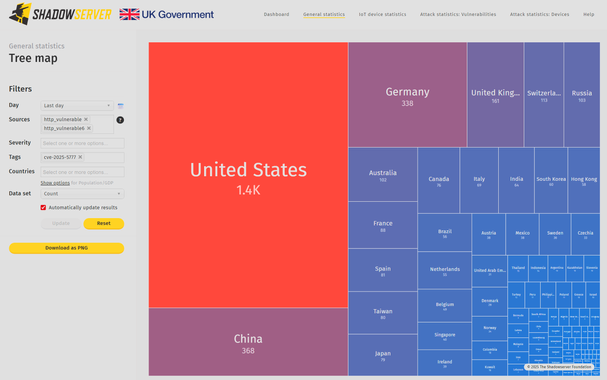
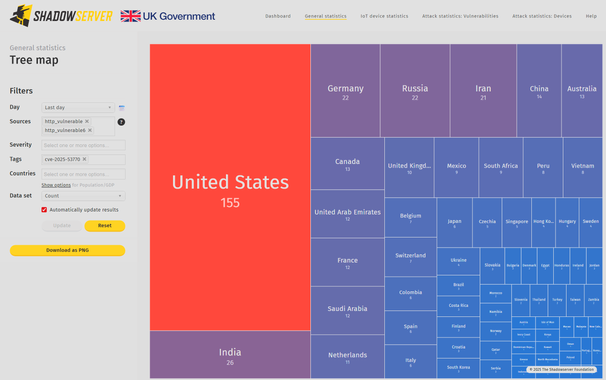
Major orgs are continuing to be accessed via #CitrixBleed2 without realising, today.
Left: vulnerable servers to #CitrixBleed2
Right: vulnerable servers to SharePoint vuln you've all read about
The SharePoint vuln is actually far smaller in scope and number of victims. The cybersecurity industry is asleep at the wheel.
Talos write-up on Chaos. TTPs in the post.
https://blog.talosintelligence.com/new-chaos-ransomware/
Talos assesses with moderate confidence that the new Chaos ransomware group is either a rebranding of the BlackSuit (Royal) ransomware or operated by some of its former members. This assessment is based on the similarities in TTPs, including encryption commands, the theme and structure of the ransom note, and the use of LOLbins and RMM tools in their attacks.
And IOCs in their repo:
A crucial government cybersecurity contract has expired on Sunday.
The CyberSentry program monitored for malicious activity on the IT and OT networks of US critical infrastructure operators
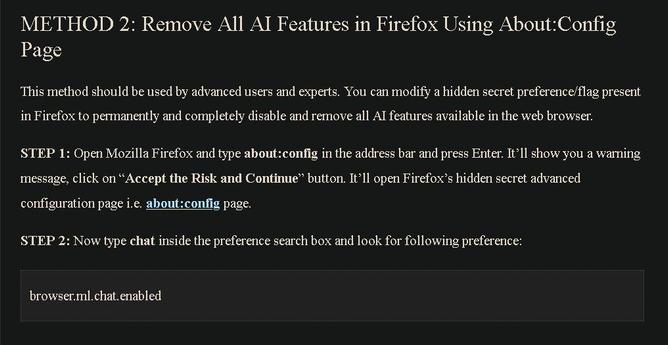
Remove All AI Features in Firefox Using About:Config Page
1/Open Mozilla Firefox & type about:config in the address bar & press Enter. It’ll show you a warning message, click on “Accept the Risk & Continue” button
2/Type "browser.ml.chat.enabled" inside the preference search box
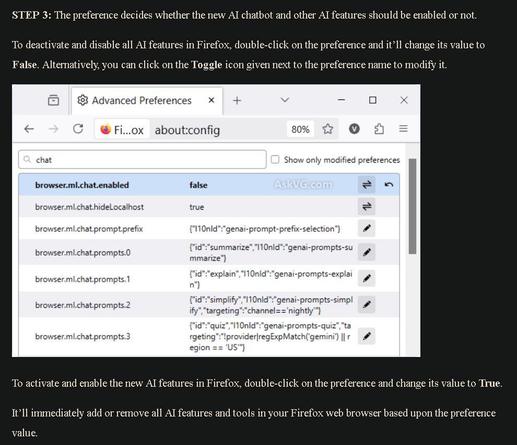
3/To deactivate & disable all AI features in Firefox, double-click preference & it’ll change its value to False
https://www.askvg.com/how-to-disable-and-remove-all-ai-features-in-mozilla-firefox/
-
-
This is for desktop as I got rid of my smartphone
I'M MUTING THIS
The Gift of Life
4pm friday afternoon!
everyone push to prod and leave early! gogogogo!
start that compile! launch that deploy! stop watching the github action progress text! reboot the domain controller and the firewall at the same time! cycle all the saml tokens! clear all cached creds! flee to the woods!
Don't tie your identity to your job. Jobs are temporary, often ending unpredictably. When your identity is your work, your mental health is impacted horribly when your job security is at risk or you get let go.
I've seen multiple folks in cyber suffer from this, some barely surviving the ordeal.