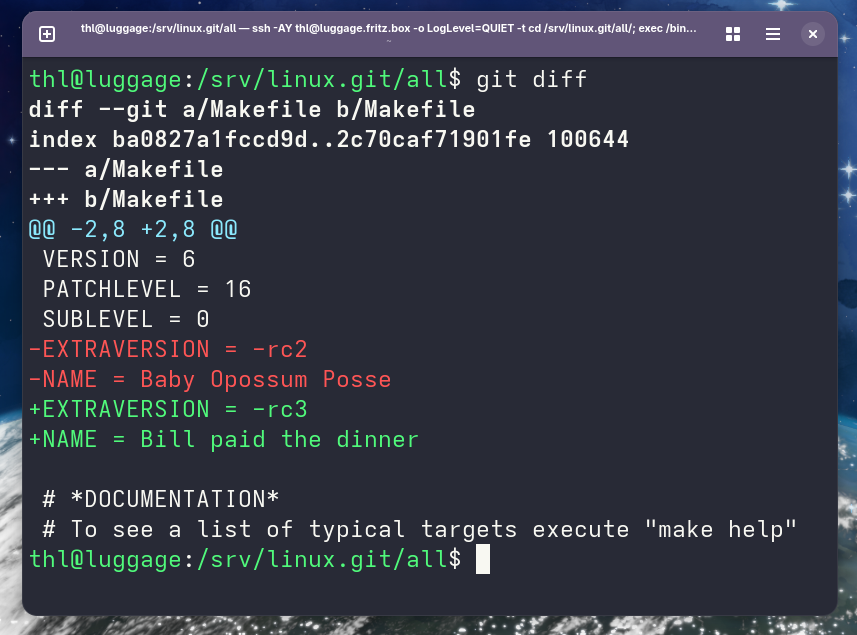
WDYT @cadey ? What is the end game?
Linux dev. Android user. Security curious. Gopher hobbyist. Beginner rustacean. Casual hardcore gamer. — French native, english toots — Personal account — He/him.
Posts in CC-BY-ND for a month, then CC-BY-NC-ND, contact me for other arrangements.
Profile picture is a line drawing caricature by french artist Frank Tizzoni of myself; I have a french-style flat cap and a light beard.
| website | https://anisse.astier.eu |
| Kernel Recipes 2022 liveblog | https://kernel-recipes.org/en/2022/category/live-blog/ |
| Kernel Recipes 2023 liveblog | https://kernel-recipes.org/en/2023/category/live-blog/ |
| Message me on Signal | https://signal.me/#eu/y7Yv18foRXDoXscEQlKOEY5G899AwTr8Mlp0wO0eU3hN3pSM3JtEWJpwudNLxfXz |