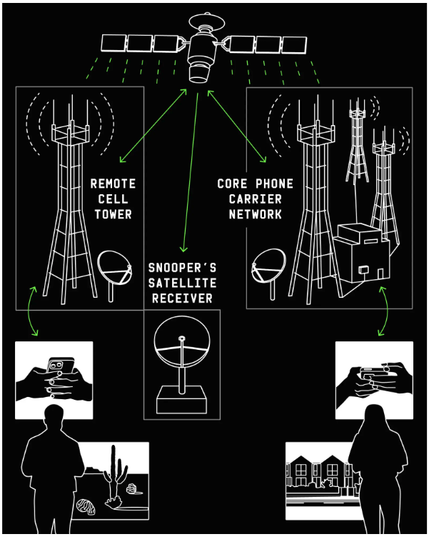
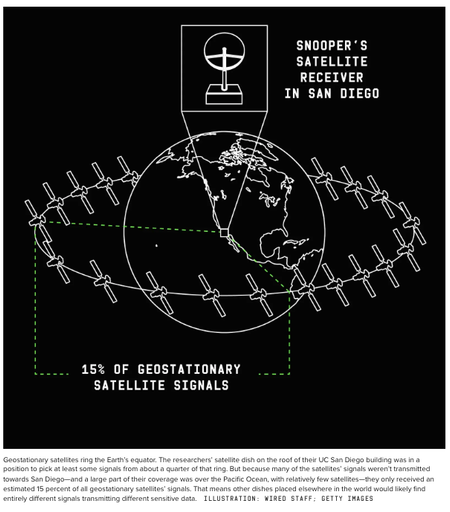
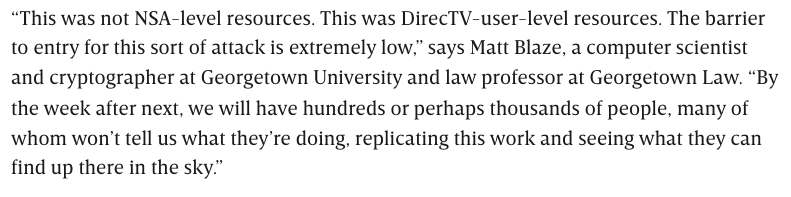
That means a dish in a different place would pick up entirely different data. Probably an entirely different stream of unencrypted secrets.
As @mattblaze told me:
I personally think that, from this summary, since this is Starlink partnering with a German telecom giant (T-Mobile the American arm of Deutcshe Telecom in my eyes), that nonsense in unencrypted intentionally, and they may not want it turned on for "security reasons" or some nonsense like that.
This means that you have to encrypt that stuff yourself using software already available. Better yet, encrypt your sensitive stuff before it gets sent.
That's a cool article! Kudos to T-Mobile for patching their shit when they were informed of the issue.
Also yes Mugita; T-Mobile is owned by Deutsche Telekom. That's no secret.
Additionally, they talk heavily of public-access phone calls and text messages; both of which are transmitted on the public teleco network. Again it's no secret that phone calls and SMS messages lack proper security; they have lacked proper security since the 1980's and I don't foresee them changing their policies anytime in the future.
Take cell phones for example; they usually use encryption to connect to the tower, but will gladly connect to an unencrypted node with not even a notification to the user.
Intentional or not; malicious or not; just never trust third party vendors to keep your data safe. Only rely on public/private keys that you personally control. This is why I publish my public GPG keys just in the off chance someone opts to message me actually securely.
Oh yeah, and my phone does not contain my private GPG keys, because mobile phones are inherently insecure.
Sensitive Satellite Internet Data Is Easily Accessible, If You Know Where to Look
At Black Hat, an Oxford University student outlines how his team intercepted unencrypted satellite internet data across a 'massive attack area' from government agencies, major shipping companies, Greek billionaires, and more.
from only a CURSORY look at that article you posted, and the one posted by greenberg..
i would say this is the major difference, tho both studies came to similar conclusions:
the Oxford team focused on 18 satellites, and what they were broadcasting,
while this new study has used a satellite dish to pick up ANY communications from transmitting satellites that were passing over their dish
*this is just my own assumption - feel free to correct me if i'm wrong
@rustoleumlove
Nope. The article says this new research was also targeting geosynchronous satellites.
"[...] communications of geosynchronous satellites in the small band of space visible from their Southern California vantage point. By simply pointing their dish at different satellites [...]"
Gotta wonder how many Pete Hegseth texts and calls they could pick up?
getting a flashback
to that scene in Heat
where the guy is proposing the massive bank heist where the thieves will score millions ...
and de niro is like where did you get this information?!
and the dude replies something like: 'it's just beamed thru the air, all you have to do is grab it'
🤣 😩 🤣
(it never fails to amaze me that art is absolutely prescient but NO ONE LEARNS from it)
@agreenberg
I saw someone post this earlier, and commented then about these two articles:
Turns out, a bunch of people hijack old non-encrpted US satilites for funzies:
https://www.rtl-sdr.com/hunting-for-space-radio-pirates-on-the-us-military-flt-satcom-satellites/
and of course, certain waring parties do it:
but remember, if you're using hijacked non-encrypted satellites to communicate with each other, assume your enemy is too. 'Cause I can assure you that Ukraine does.
Hunting for Space Radio Pirates on the US Military Fleet Satcom Satellites
In the 70's and 80's the US government launched a fleet of satellites called 'FLTSATCOM', which were simple radio repeaters up in geostationary orbit. This allowed the US military to easily communicate with each other all over the world. However, the technology of the time could not implement encryption. So security relied entirely on only the US militaries technological advantage at being the only ones to have radio equipment that could reach these satellites. Of course as time progressed equipment which could reach the 243 - 270 MHz range of the satellites became common place, and the satellites began picking