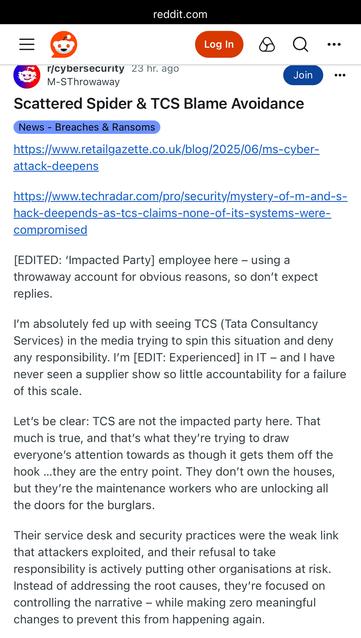
M&S have finally told staff that data about themselves was stolen: https://www.telegraph.co.uk/business/2025/05/16/ms-staff-data-stolen-by-hackers-in-cyber-attack/
You may notice I said they had staff data stolen on May 9th in this thread.
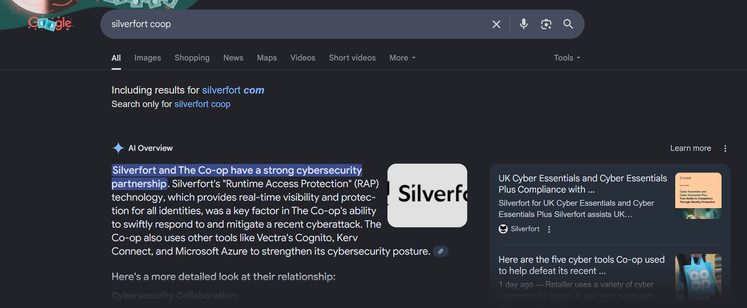
For the record, the tools listed in this article aren't used by Co-op.
The link in the article to Vectra Cognito AI has a Coop Sweden logo on it, and the Coop Sweden CISO is named. Coop Sweden is different company. Coop Sweden went on to have a ransomware attack that crippled the org, including point of sale, so I don't think it's a good sales point. Same with Silverfort.
Google AI has ingested the article and now uses it to claim Co-op Group use the tools.
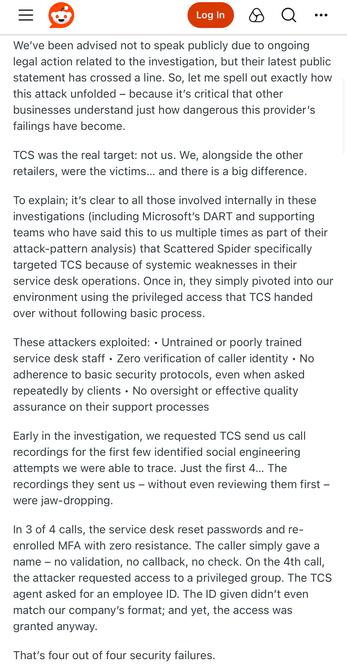
The Times reports M&S were breached through a contractor and that human error is to blame. (Both M&S and Co-op use TCS for their IT Service Desk).
The threat actor went undetected for 52 hours. (I suspect detection was when their ESXi cluster got encrypted).
M&S have told the Times they had no “direct” communication with DragonForce, which is code for they’re using a third party to negotiate - standard practice.
https://www.thetimes.com/uk/technology-uk/article/m-and-s-boss-cyber-attack-7d9hvk6ds
M&S looks to be moving to reposition their incident as a third party failure, which I imagine will help redirect some of the blame (they present their financial results during the week to investors): https://www.bbc.co.uk/news/articles/cpqe213vw3po
Both M&S and Co-op outsourced their IT, including their Service Desk (helpdesk), to TCS (Tata) around 2018, as part of cost savings.
There's nothing to suggest TCS itself have a breach btw.
Basically, if you go for the lowest cost helpdesk - you might want to follow the NCSC advice on authenticating password and MFA token resets.
I've put a 3 part deep dive blog series coming out probably next week called Living-Off-The-Company, which is about how teenagers have realised large orgs have outsourced to MSPs who follow the same format of SOP documentation, use of cloud services etc. Orgs have introduced commonality to surf.
"Cyber analysts and retail executives said the company had been the victim of a ransomware attack, had refused to pay - following government advice - and was working to reinstall all of its computer systems."
Not sure who those analysts are, but since DragonForce haven't released any data and M&S won't comment other than to say they haven't had any "direct" contact with DragonForce, I wouldn't make that assumption.
There's also a line in the article from an cyber industry person saying "if it can happen to M&S, it can happen to anyone" - it's ridiculous and defeatist given Marks and Spencer haven't shared any technical information about how it happened, other than to tell The Sunday Times it was "human error"
The Air Safety version of cyber industry would be a plane crashing into 14 other planes, and industry air safety people going "Gosh, if that can happen to British Airways it could happen to anybody!"
Tomorrow it’s one month since Marks and Spencer started containment, it’s also their financial results day.
Online ordering still down, all recruitment stopped, Palo-Alto VPNs still offline.
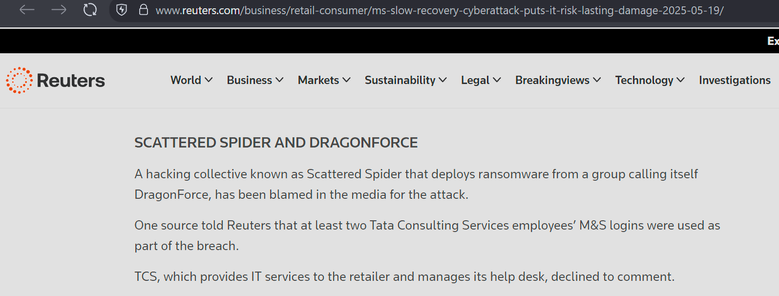
TCS have been linked to the Marks and Spencer breach, at least in part.
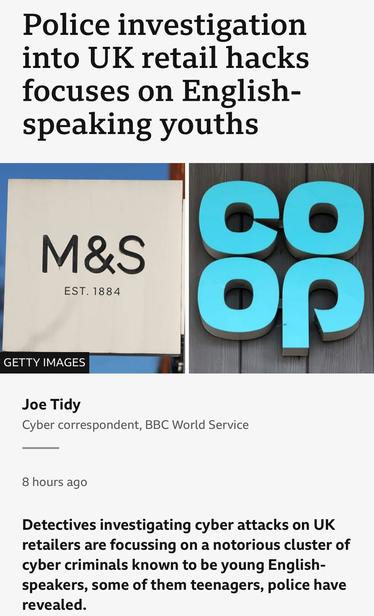
The NCA has confirmed on the record that the investigation into the M&S and Co-op hack is focused on English teenagers. I could toot the names of the people I think they’ll pick up, but won’t.
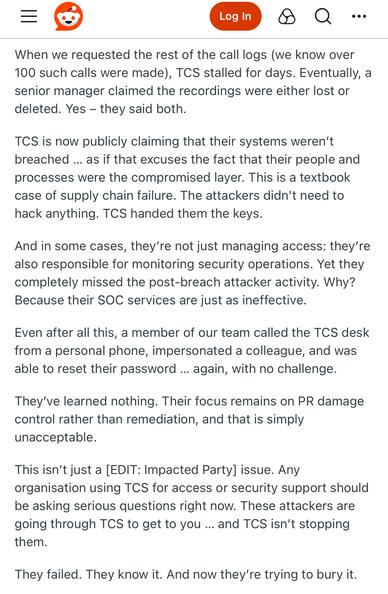
TCS has a security incident running around the M&S breach.
Interestingly the source claims TCS aren't involved in Co-op's IT - which is categorically false, they took over most of it while I worked there, including the helpdesk, and my team (SecOps) after I left.
https://www.ft.com/content/c658645d-289d-49ee-bc1d-241c651516b0
Insurance Insider say Co-op Group have no cyber insurance policy.
It’s got the insurance industry hard as they think they can ambulance chase other orgs with it.
While Co-op have restored every customer facing system and internal systems like recruitment and remote working, M&S still don't even have recruitment back.
I'm reliably told they paid the ransom, so they'll be target #1 basically forever with other ransomware groups now due to resiliency woes and willingness to pay.
https://www.bbc.co.uk/news/articles/c23mz5eg091o
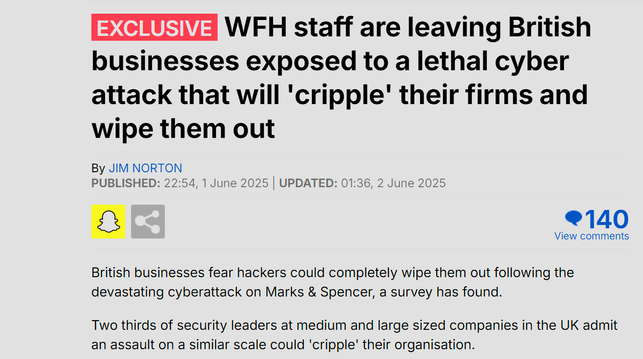
This Daily Mail piece about security leaders thinking work-from-home means they will be crippled is horseshit, I'm not linking it.
They've taken a survey about how security people think their businesses couldn't survive ransomware, and linked it to working from home. WFH isn't the problem: business IT and resilience being built on quicksand is the problem.
Co-op say they have largely completed recovery, and have removed the cyber attack banner and statement from their website
https://www.retailgazette.co.uk/blog/2025/06/co-op-cyber-attack/
I think they did a great job. They do call it a "highly sophisticated attack", which, frankly.. isn't true and may come out in open court later if the suspects are ever caught.
6 weeks from containment to "near full" recovery, for statto nerds like me who track this stuff.
M&S had their ransomware incident communicated via internal email - from the account of a staff member who works for TCS.
The way TCS work is you give them accounts on your AD.
Marks and Spencer have started partial online shopping again.
For statto nerds, around 7 weeks from containment to partial recovery
TCS have told shareholders their systems were not compromised in the hack of M&S.
As an explainer here (not in the article): TCS IT systems weren't compromised. Their helpdesk service (they're AD admins at M&S) was used to gain access to M&S. They manage M&S IT systems.
https://www.reuters.com/business/media-telecom/indias-tcs-says-none-its-systems-were-compromised-ms-hack-2025-06-19/
Latest Marks and Spencer update is pretty crazy.
M&S haven't been able to supply sales data - so the British Retail Consortium (BRC) - used by the UK government as as economic indicator - basically made up figures for M&S and didn't tell people they had done this.
https://www.telegraph.co.uk/business/2025/06/24/retail-lobby-group-accused-of-ms-cyber-cover-up/
Marks and Spencer’s CEO says half of their online ordering is still offline after their ransomware incident, they hope to get open in next 4 weeks.
They are also rebuilding internal systems and hope a majority of that will be done by August.
Lesson: mass contain early. M&S didn’t. Co-op did.
17 and two 19 year old teens picked up over Co-op and M&S hacks, and a 20 year old woman.
Pretend to be surprised.
. @briankrebs has broken the story that the key member (and teenager) of LAPSUS$ runs Scattered Spider
https://krebsonsecurity.com/2025/07/uk-charges-four-in-scattered-spider-ransom-group/
Co-op finally admitted the entire membership database was stolen
I had this in the thread months ago, they originally tried to deny it entirely then tried to say ‘some’ data was accessed when they knew it was the whole thing.
Personally I think Co-op did a really good job getting out of that situation and minimising impact.
I definitely think if you have a LAPSUS$ style advanced persistent teenagers situation, tilt towards open and honest comms as those kids will use secrecy against ya. It’s 2025, it’s okay to say you got hacked, people largely understand. Also, in IR, lawyers are usually stuck in 1980 advice - it’s just advice, they ain’t yo boss.
The people arrested as part of the Co-op and M&S hack investigation have been released on bail.
Previously when this happened with LAPSUS$, they just continued hacking stuff.

Four people bailed after arrests over cyber attacks on M&S, Co-op and Harrods
Four young people who were arrested for their suspected involvement in the damaging cyber attacks against Marks & Spencer, the Co-op and Harrods, have been bailed. The arrests on July 10 included a 17-year-old British man from the West Midlands, a 19-year-old Latvian man from the West Midlands, a 19-year-old British man from London, and […]
It’s 2025, it’s okay to say you got hacked, people largely understand.
Probably the most damning indictment of the entire computing industry that I've seen for a long time.
I don't disagree at all. But this absolutely should not be the case and wouldn't be if we weren't still building core infrastructure around ideas that were known to be bad by the mid 1980s.
@david_chisnall @GossiTheDog It would still happen. It would be different, no question, but logic errors are not solved by infrastructure, neither is the malicious intend.
Companies being hacked is quite close to car accidents. You have many individuals that manage devices that can do potential harm. There is a limited ability to enforce all rules to all individuals without breaking necessary loopholes in the system to work.
We do live with car accidents and we learn from them. It's all human.
@sheogorath @david_chisnall @GossiTheDog
When I'm driving I'm extremely careful because a crash can have life changing consequences for the people involved and the law rightly takes it seriously. I think we need to start treating cyber security the same way.
I'm not sure developers and companies always appreciate the scale of harm when things go wrong. Thousands of people work on car design to ensure safety. The fact that people can survive a 70mph crash is astonishing. Maybe it's time we ensure engineering principles are at the heart of software development outside of university.
@tigerhiddenadam @david_chisnall @GossiTheDog Agreed, but we also have to keep in mind that software development has this strict oversight e.g. in the car industry. IT is a helper technology. The same way not all bolds need to withstand forces of a space ship liftoff, not all IT has to withstand the most targeted attacks.
Should we improve it? Yes. Does this already happen? In some parts.
My point here: maybe we have to look at relevant industries and processes rather than IT on its own ;)
@sheogorath @tigerhiddenadam @GossiTheDog
Imagine I write a privilege separated application, where one process talks to the network but has no access to secrets and all of the others are bug free (ignore that this bit is probably impossible).
There is not one single mainstream operating system that I can point to and say: if the networked process is compromised then secrets will not be leaked. seL4 is able to make this guarantee (except for hardware side channels) but has a programmer model that makes it impossible to build large systems on it with useful security properties.
I consider that to be an IT industry problem. You can't do engineering of systems if you can't depend on any of your components.
- cars mostly need to withstand random events (acts of nature, stupid humans) while internet-exposed software needs to withstand clever adversaries.
- we have no particular separation between software that is "internet-certified" and not, nor do we separate developers into such classes.
- we have near-term cost pressures to cut corners; to use unsafe languages, to write unsafe code, "for performance".