The Russians aren't coming, they are already here. Without most anyone realizing, they've created an entire malicious adtech industry whose story is just as complex as the Chinese organized crime we're now realizing from their ventures into pig butchering.
VexTrio is just one Russian organized crime group in the malicious adtech world, but they are a critical one. They have a very "special" relationship with website hackers that defies logic. I'd put my money on a contractual one. all your bases belong to russian adtech hackers.
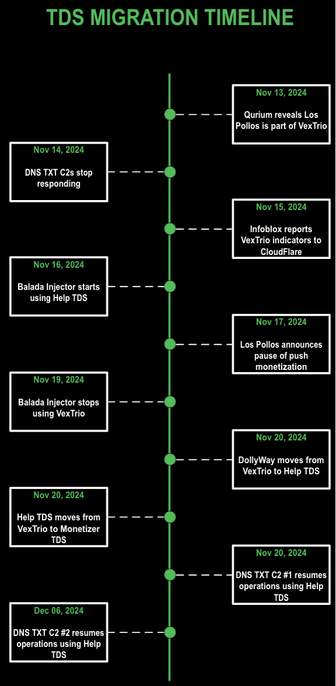
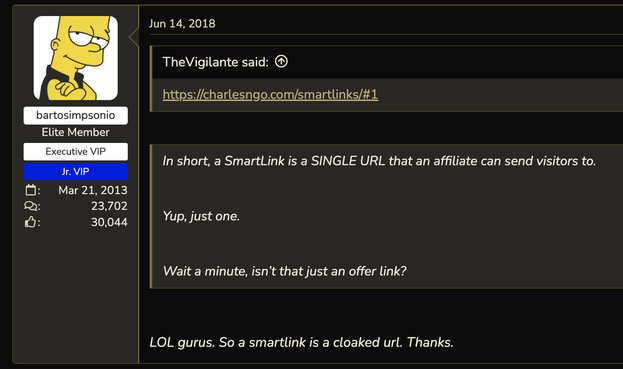
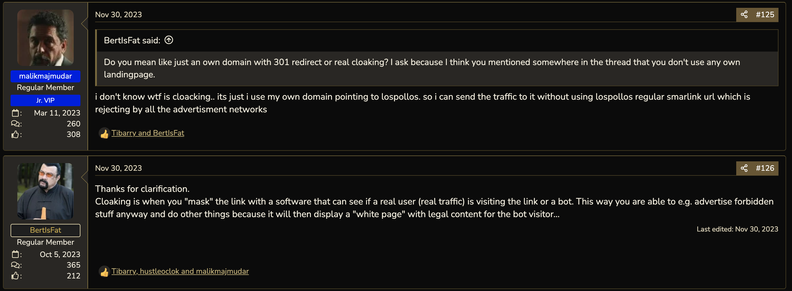
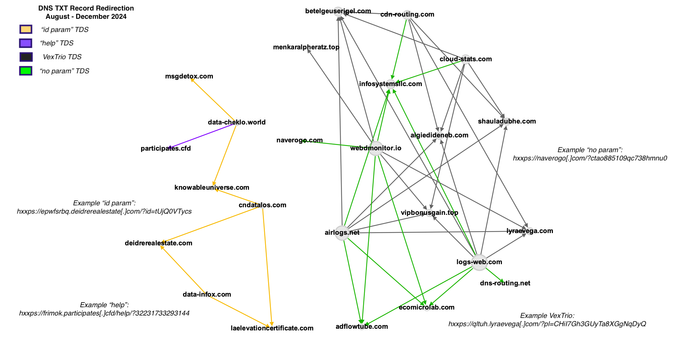
Today we've released the first piece of research that may eventually prove whether I am right. This paper is hard. i've been told. I know. We've condensed thousands of hours of research into about 30 pages. @briankrebs tried to make the main points a lot more consumable -- and wrote a fabulous complimentary article : read both!
There's so much more to say... but at the same time, between ourselves and Brian, we've released a lot of lead material ... and there's more to come. I've emphasized the Russian (technically Eastern European) crime here, but as Brian's article points out there is a whole Italian side too. and more.
We've given SURBL, Spamhaus, Cloudflare, Domain Tools, several registrars, and many security companies over 100k domains. They are also posted on our open github.
Super thanks to our collaborators at Qurium, GoDaddy Sucuri Security, and elsewhere.
#threatintel #scam #tds #vextrio #cybercrime #cybersecurity #infosec #dns #infoblox #InfobloxThreatIntel #malware #phishing #spam
https://krebsonsecurity.com/2025/06/inside-a-dark-adtech-empire-fed-by-fake-captchas/