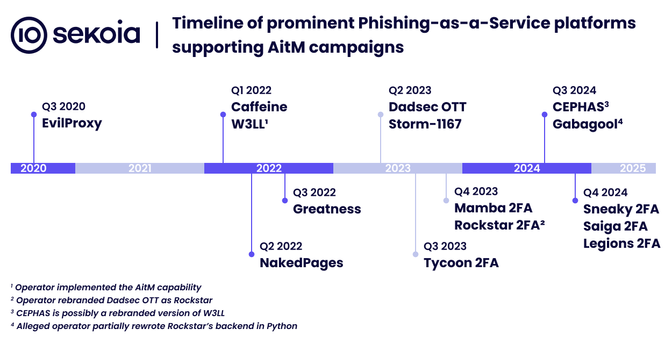
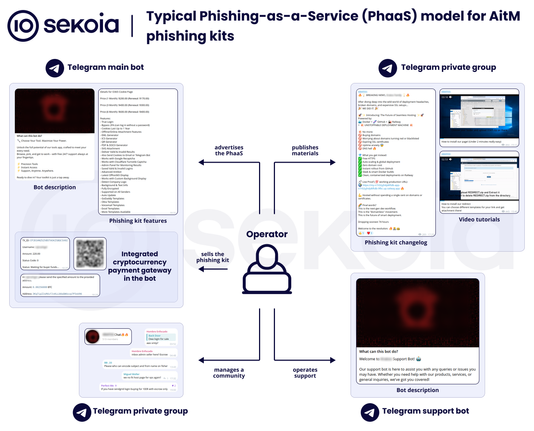
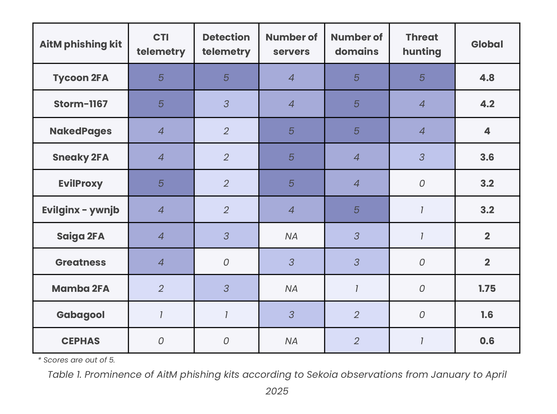
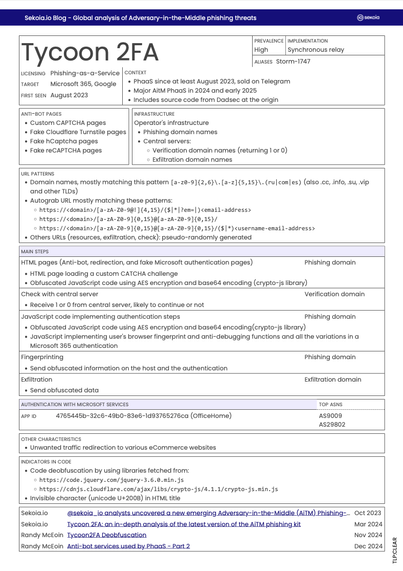
🔍 Phishing-as-a-Service (#PhaaS) is driving a wave of large-scale, sophisticated attacks against organisations.
In our new blogpost, we provide an overview of the key techniques, tactics and social engineering schemes that cybercriminals use in AitM phishing attacks.