Co-op's AGM is this weekend, and M&S yearly results and investor contact are next week.
Gonna be awkward for different reasons, e.g. Co-op is member (customer) owned, so the people's data Co-op had stolen are effectively the shareholders and are invited.
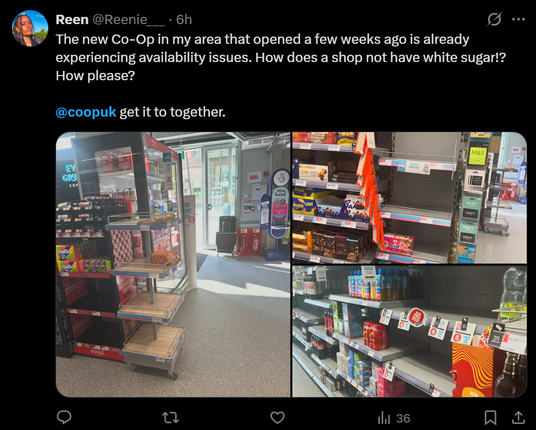
The Grocer reports Nisa and Costcutter are running out of fruit & veg, fresh meat and poultry, dairy products, chilled ready meals, snacks and desserts.
Nisa and Costcutter are supplied by Co-op Wholesale, which is dependent on Co-op Group.
“It’s really poor. I feel bad for them but what makes it worse is their hush-hush mentality about it. There’s no proper level of communication and we get random updates.”
Co-op Wholesale claim there are no problems. https://www.thegrocer.co.uk/news/nisa-and-costcutter-hit-by-stock-shortages-amid-co-op-cyberattack/704393.article
Co-op Group have told their suppliers that "systemic-based orders will resume for ambient, fresh, and frozen products commencing Wednesday 14 May". They say forecasting system will still be impacted.
https://www.thegrocer.co.uk/news/co-op-to-get-systems-back-on-track-after-cyberattack/704425.article
Co-op Group say they have exited containment and begun recovery phase https://www.theguardian.com/business/2025/may/14/co-op-cyber-attack-stock-availability-in-stores-will-not-improve-until-weekend
Marks and Spencer are still in containment
If you want figures for your board to set expectations in big game ransomware incidents, Co-op containment just over 2 weeks, M&S just over 3 weeks so far - recovery comes after.
In terms of external assistance, Co-op have Microsoft Incident Response (DART), KPMG and crisis comms. M&S have CrowdStrike, Microsoft, Fenix and crisis comms.
The threat actor at Co-op says Co-op shut systems down, which appears to have really pissed off the threat actor. This was the right, and smart, thing to do.
While I was at Co-op we did a rehearsal of ransomware deployment on point of sale devices with the retail team, and the outcome was a business ending event due to the inability to take payments for a prolonged period of time. So early intervention with containment was the right thing to do, 100%.
M&S have finally told staff that data about themselves was stolen: https://www.telegraph.co.uk/business/2025/05/16/ms-staff-data-stolen-by-hackers-in-cyber-attack/
You may notice I said they had staff data stolen on May 9th in this thread.
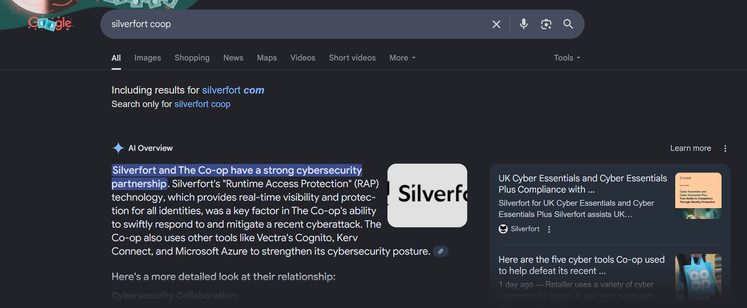
For the record, the tools listed in this article aren't used by Co-op.
The link in the article to Vectra Cognito AI has a Coop Sweden logo on it, and the Coop Sweden CISO is named. Coop Sweden is different company. Coop Sweden went on to have a ransomware attack that crippled the org, including point of sale, so I don't think it's a good sales point. Same with Silverfort.
Google AI has ingested the article and now uses it to claim Co-op Group use the tools.
The Times reports M&S were breached through a contractor and that human error is to blame. (Both M&S and Co-op use TCS for their IT Service Desk).
The threat actor went undetected for 52 hours. (I suspect detection was when their ESXi cluster got encrypted).
M&S have told the Times they had no “direct” communication with DragonForce, which is code for they’re using a third party to negotiate - standard practice.
https://www.thetimes.com/uk/technology-uk/article/m-and-s-boss-cyber-attack-7d9hvk6ds
M&S looks to be moving to reposition their incident as a third party failure, which I imagine will help redirect some of the blame (they present their financial results during the week to investors): https://www.bbc.co.uk/news/articles/cpqe213vw3po
Both M&S and Co-op outsourced their IT, including their Service Desk (helpdesk), to TCS (Tata) around 2018, as part of cost savings.
There's nothing to suggest TCS itself have a breach btw.
Basically, if you go for the lowest cost helpdesk - you might want to follow the NCSC advice on authenticating password and MFA token resets.
I've put a 3 part deep dive blog series coming out probably next week called Living-Off-The-Company, which is about how teenagers have realised large orgs have outsourced to MSPs who follow the same format of SOP documentation, use of cloud services etc. Orgs have introduced commonality to surf.
Argh, flashbacks to trying to convince directors that outsourcing IT is bad. Very bad.
@GossiTheDog “we aren’t a computer company, so off to India / China / Vietnam / Philippines / etc for all this non-core-business shit”
…
“Why company not run without computers? Who did this?”
@GossiTheDog to be fair, IIRC, Coop Sweden went down because their payment provider used Kaseya.
So, it was ransomware on a fourth party, nothing Coop Sweden had any direct control over
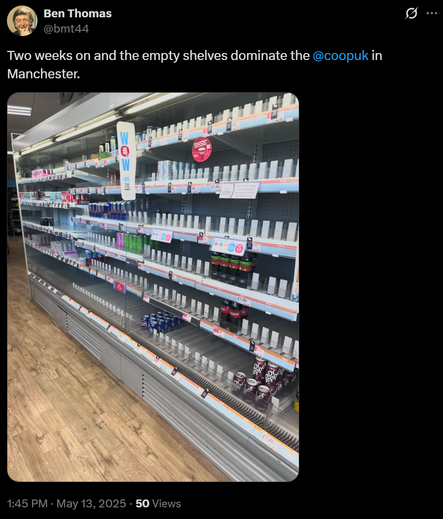
This was yesterday evening in my local co-op store (close to central Manchester.) Still lots of empty spaces on the shelves.
The quote
> They torched shareholder value
made me laugh
they have no idea what the Coop is
Just glad some of the lessons sank in....
Ambient is shop-speak for stuff that is kept at room temperature. So biscuits, tea and coffee, tinned stuff, etc.
@GossiTheDog, TP;DR.
(Too portrait; didn't watch.)
@GossiTheDog the thieves could probably show up at the AGM and present themselves as a member, since they have access to all the information the Co-Op has on it's membership...number, address, etc.
Short of checking govt. ID or requiring a hard copy of the meeting invite that was mailed to their address. Even then, the thieves might've gotten away with that too.
@johnefrancis @GossiTheDog
Members who wanted to attend were supposed to indicate this on the agm voting form, which closed midday yesterday. I might have tried, but forgot to go back to it until too late..
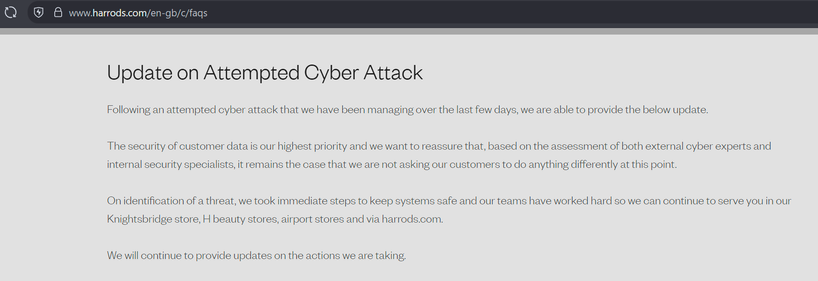
I've not had any emails from coop about this, despite being a member. Nor from M&S, though I'm only registered on their app. (I can also continue to ignore Harrods, never having used them!)
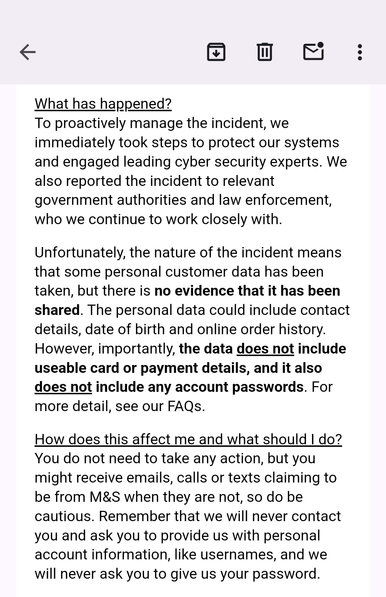
And 45 mins later I get an email from M&S. Nice of them to reassure us that none of the stuff I can change, like bank cards, was stolen. Only the things I can't change, like date of birth.