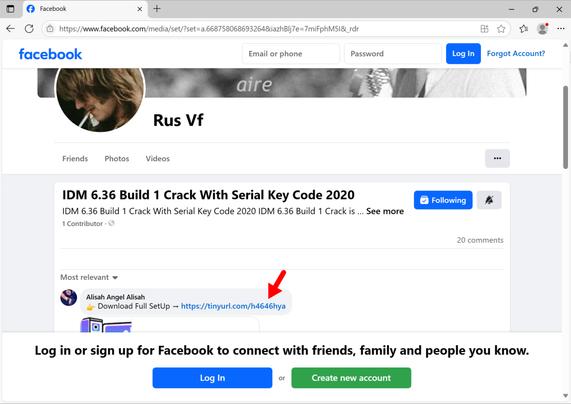
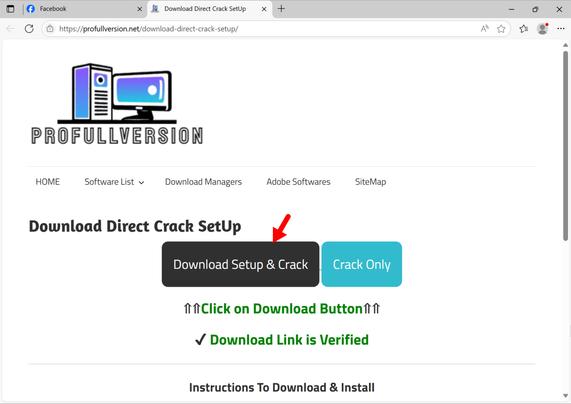
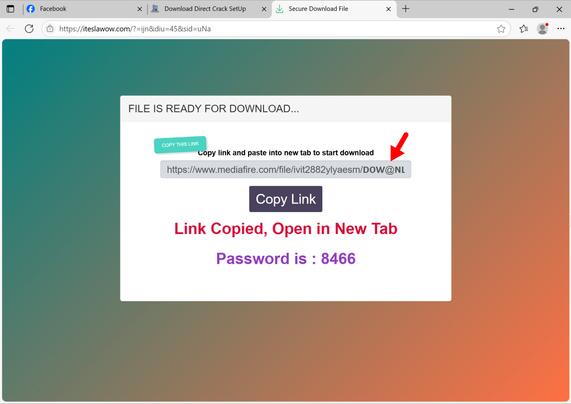
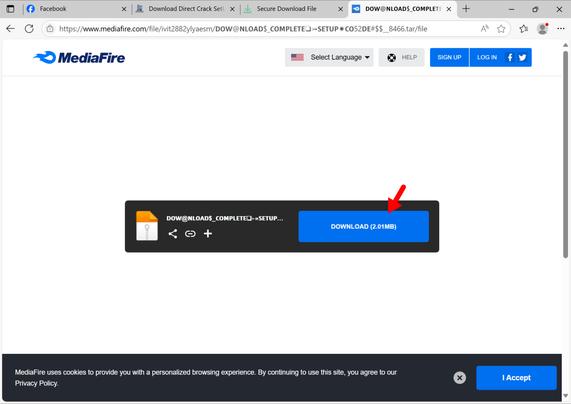
2025-05-22 (Thursday): After the recent #LummaStealer disruption, I found an active sample today, so how effective was the disruption, really?
SHA256 hash for the installer EXE for Lumma Stealer:
8619bea9571a4dcc4b7f4ba494d444b8078d06dea385dc0caa2378e215636a65
Analysis:
- https://tria.ge/250523-afpxxsfm5t
- https://app.any.run/tasks/add82eaa-bdb8-43b9-885b-c0a58cc2530c
To be fair, I investigated a campaign that was pushing Lumma Stealer earlier this week, and it had switched to #StealC v2 malware earlier today (2025-05-22):
So the disruption was at least somewhat effective based on what I'm seeing. I don't have eyes on the criminal underground, though, so I don't know what's happening with Lumma Stealer's customers.