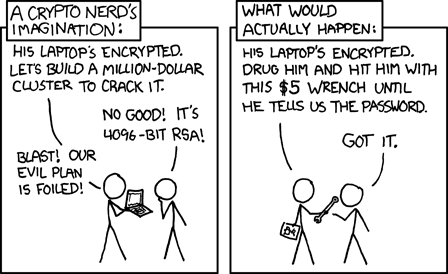
Ok, here's the deal on the "YubiKey cloning attack" stuff:
 Yes, a way to recover private keys from #YubiKey 5 has been found by researchers.
Yes, a way to recover private keys from #YubiKey 5 has been found by researchers.
But the attack *requires*:
👉 *physically opening the YubiKey enclosure*
👉 physical access to the YubiKey *while it is authenticating*
👉 non-trivial electronics lab equipment
I cannot stress this enough:
✨ In basically every possible scenario you are safer using a YubiKey or a similar device, than not using one. ✨




 tonic
tonic