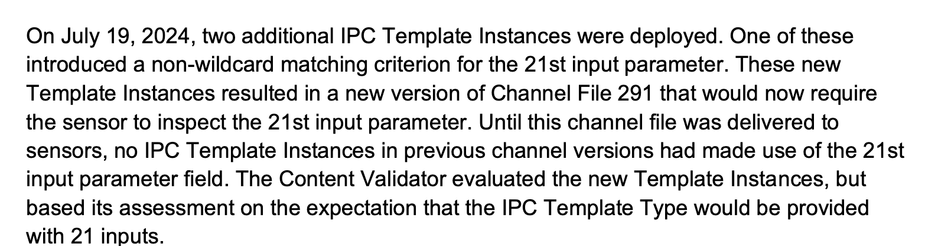
So what's that -mean- anyway?
So you have the sensor - that is, the specific bit of software from CS that is installed on your endpoint.
And what that sensor does is correlate "context from its local graph store" - telemetry events that it's got in a database - into "behaviors and indicators of attack"
So it matches behavioral patterns.
And then it talks about "Rapid Response Content" that gets delivered from 'the cloud' to provide behavioral definitions "without requiring sensor code changes"
..........wait what.
Why would you need your -sensor- to have a code change to update what it looks for. This is why we have configuration files and definition files as a concept.
Anyway, this 'Rapid Response Content' is about "behavioral heuristics" which --
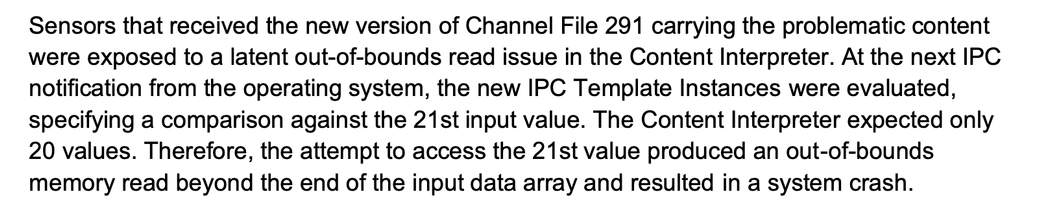
Oh hey! As it happens, my actual literal job is making that specific thing for a competitor.
So I can tell you that the way that -I- do this is to look at the behavior of the malware under analysis, and chart out what it does - what files it accesses, what devices it hits, what signals it gets involved with, what system calls it makes, what libraries it's linked to, etc. - and then look into the context of what a -normal- workflow would look like in related areas, and then find the differences.
And from those differences I make a nice lil YAML file that gets sent to the sensor, that it uses to make those kinds of correlations between events and "things to be worried about".
There's, y'know, a whole-ass testing process involved before that happens, but we'll get there.
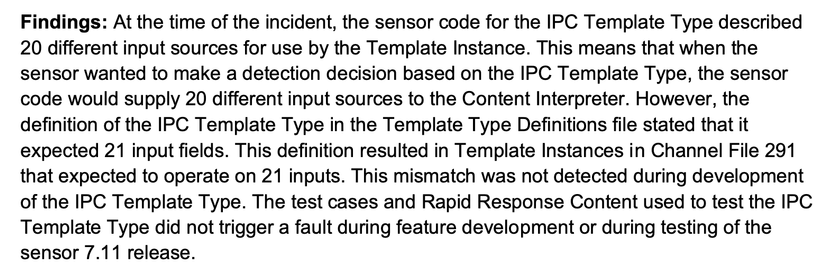
The "Rapid Response Content" is the same shape as this - it gets sent to the endpoints "via the cloud" (a set of servers) and it changes the behavior of the endpoint sensor to look for specific behaviors.














 💲Paid
💲Paid