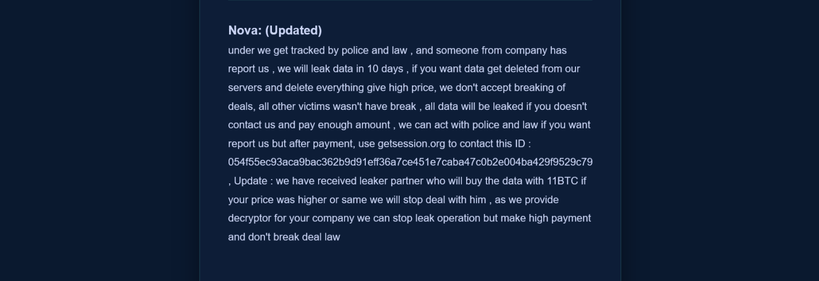
NEW by me: Idaho man who threatened his hacking victims appeals his sentence in Georgia:
This is an appeal by Robert Purbeck, aka "Lifelock" aka "Studmaster."
It is an interesting case to watch because the judge was so disturbed by the defendant's threatening emails to his victims and references to the victims' children that he did not impose the sentence the prosecution had recommended as part of the plea deal. He sentenced Purbeck to the maximum the law allowed, which was even higher than the upper end of the sentencing guidelines for the defendant's offense level.
Purbeck appealed on the grounds that the prosecutor had a duty to really advocate for the sentence agreed to in the plea deal but the prosecutor used inflammatory language and portrayed the defendant as an ongoing threat. There's also a second issue on appeal that I predict the defendant will prevail on as the special conditions of release announced in the sentencing hearing do not match what was published in the docket later.
But what this appeal really made me think about is whether there is anything in calculating offense level that adds levels if a hacker/threat actor threatens the victims. If there already is something like that, it wasn't factored into this defendant's offense level. Can any federal prosecutors, former federal prosecutors, or judges clarify that for me?
https://databreaches.net/2025/09/05/idaho-man-who-threatened-his-hacking-victims-appeals-his-sentence-in-georgia/
#databreach #extortion #healthsec #RobertPurbeck #Lifelock #11CA