🛡️ DHCP Snooping: First Line of Defense in L2 Security
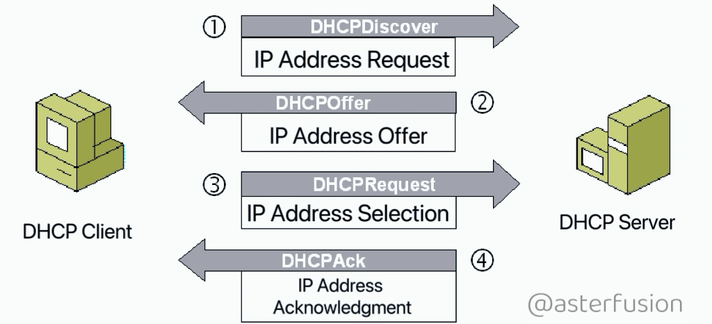
Rogue DHCP servers can poison your network, assign fake IPs, and redirect traffic. DHCP Snooping protects against this by:
• Validating DHCP messages via trusted ports
• Building a binding table for IP–MAC–VLAN mappings
• Blocking untrusted responses at the switch level
It’s simple, effective, and essential for campus & enterprise networks.
📘 Learn how it works, where to deploy, and what hardware supports it:
🔗 https://cloudswit.ch/blogs/what-is-dhcp-snooping-and-how-does-it-work/
#DHCPsnooping #L2Security #NetworkSecurity #Switching #ZeroTrust #CloudSwit #EnterpriseNetworking #TrustedAccess #SONiC
What Is DHCP Snooping And How Does It Work? - Asterfusion Data Technologies
This article explains what DHCP Snooping is and how it works, dives deep into the technical details behind the feature, and walks you through how to configure DHCP Snooping on Asterfusion’s SONiC-based open network switches.
