My summer associate Michael Lin wrote a powershell script to help you find out which vulnerable/malicious drivers from loldrivers.io will successfully load on your HVCI-enabled system: https://github.com/trailofbits/HVCI-loldrivers-check
Yarden Shafir
@yarden_shafir@infosec.exchange
- 696 Followers
- 47 Following
- 64 Posts
@Rairii fixed :)
As of build 25915 (latest Preview) all known API based kernel address leaks no longer work unless requested by a process with SeDebugPrivilege (only available to admin processes)
Monday morning red teaming tip: look at the json files in your Windows system and where they're used
Want to practice your kernel VR and exploitation skills?
Pick any driver from the HVCI driver block list and see what you can find.
Here for example is NCHGBIOS2x64.sys that has some pretty clear issues (systemBuffer is user input):
Pick any driver from the HVCI driver block list and see what you can find.
Here for example is NCHGBIOS2x64.sys that has some pretty clear issues (systemBuffer is user input):
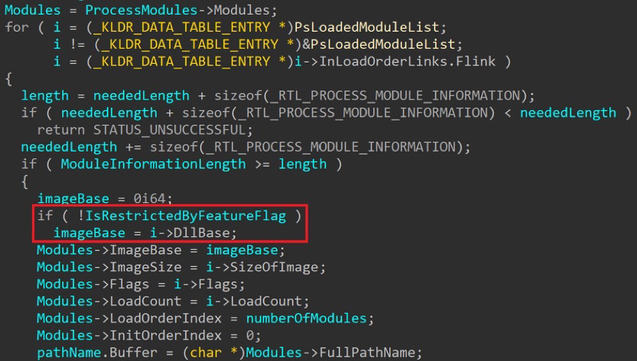
Microsoft is preparing to kill many known KASLR bypasses in the next release. Unless the calling process has debug privilege enabled, kernel addresses will be stripped from the output data of all leaking NtQuery APIs.
One example: if the caller should not receive kernel addresses, calling NtQuerySystemInformation will SystemModuleInformation class will not leak kernel image base addresses.
One example: if the caller should not receive kernel addresses, calling NtQuerySystemInformation will SystemModuleInformation class will not leak kernel image base addresses.
@hacks4pancakes so you’re not too shocked then 🤣
Hope you’re also getting ti see some of the better sides of the country!
Hope you’re also getting ti see some of the better sides of the country!
@hacks4pancakes you’re all getting the full middle eastern experience, protests and political instability included 😅
@hacks4pancakes yay! Glad you managed to make it here 😄
@hexnomad ok never mind I changed my mind