As of build 25915 (latest Preview) all known API based kernel address leaks no longer work unless requested by a process with SeDebugPrivilege (only available to admin processes)
Yarden Shafir
@yarden_shafir@infosec.exchange
- 696 Followers
- 47 Following
- 64 Posts
Want to practice your kernel VR and exploitation skills?
Pick any driver from the HVCI driver block list and see what you can find.
Here for example is NCHGBIOS2x64.sys that has some pretty clear issues (systemBuffer is user input):
Pick any driver from the HVCI driver block list and see what you can find.
Here for example is NCHGBIOS2x64.sys that has some pretty clear issues (systemBuffer is user input):
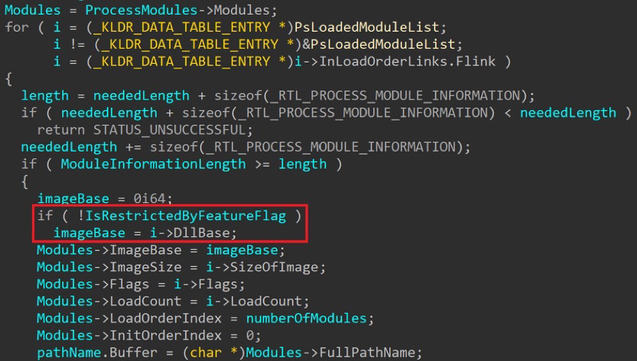
Microsoft is preparing to kill many known KASLR bypasses in the next release. Unless the calling process has debug privilege enabled, kernel addresses will be stripped from the output data of all leaking NtQuery APIs.
One example: if the caller should not receive kernel addresses, calling NtQuerySystemInformation will SystemModuleInformation class will not leak kernel image base addresses.
One example: if the caller should not receive kernel addresses, calling NtQuerySystemInformation will SystemModuleInformation class will not leak kernel image base addresses.
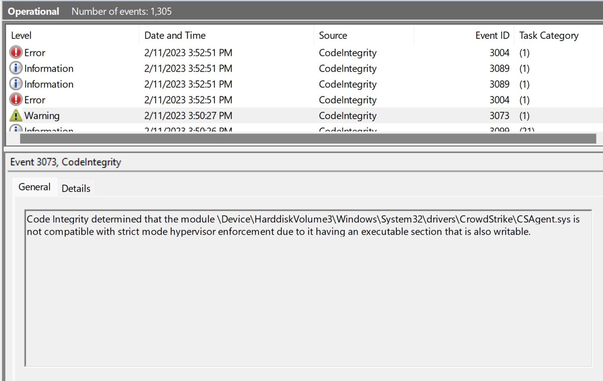
Me: 1
EDR driver: 0
(the driver doesn’t really have a RWX section)
This is what defeat looks like
I never meant to become a security researcher. My computers just refuse to behave so I have to go investigate every time.
These aren't 2 separate Windows - WinDbg is just going through a personality crisis at the moment.
These aren't 2 separate Windows - WinDbg is just going through a personality crisis at the moment.
Today's post for those of you interested in debugging, memory forensics, and obscure driver communication methods: https://windows-internals.com/investigating-filter-communication-ports/
I am now the strange person standing in the middle of the street staring at a tree (ok fine I was always that person).
But look at those icicles!!
But look at those icicles!!
This accidental bridge is very clearly the beginning of a really cool side quest
Went out to nature and found an extremely photogenic cat