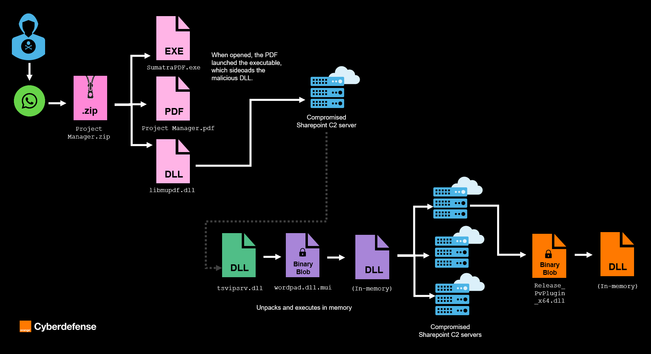
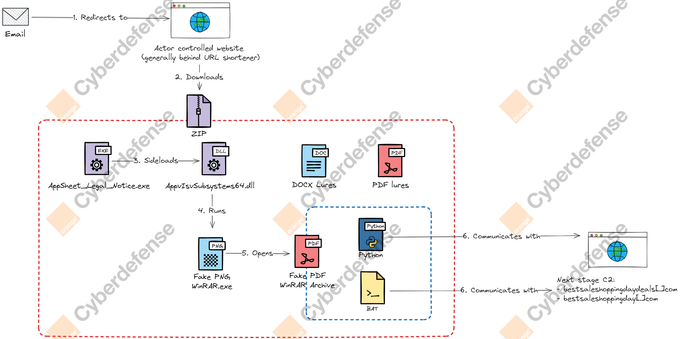
Anyone watching our research outputs over the last while, you'll note that we've been thinking a lot about taxonomies or network diagrams.
Take a look at our Cybercrime Now ecosystem graph for example -
https://research.orangecyberdefense.com/now/
-
or explore our interactive report on how China unites state, corporate, and academic assets for cyber offensive campaigns -
https://research.cert.orangecyberdefense.com/hidden-network/map.html
We hope that both these outputs will educate and benefit you in your own work, but they also represent a milestone in our ongoing effort to understand and communicate the environments in which our adversaries, whether state-backed or criminal, operate.
With this in mind, I'm very interested to hear about any other research or outputs that have succeeding in creating or discussing useful taxonomies, ontologies or network graphs of crime or cybercrime ecosystems.
From conversations with the WEF ATLAS team, it's become apparent that we don't have the full view of relevant taxonomies or ontologies that might already be defined for this purpose, or indeed already be "out there" somewhere.
So... if you've seen other work like this somewhere else, or you know of standards for these kinds of taxonomies, or research on how they should be approached, we'd love to hear about it!
#CyberSecurity #CyberCrime #ThreatIntelligence #network