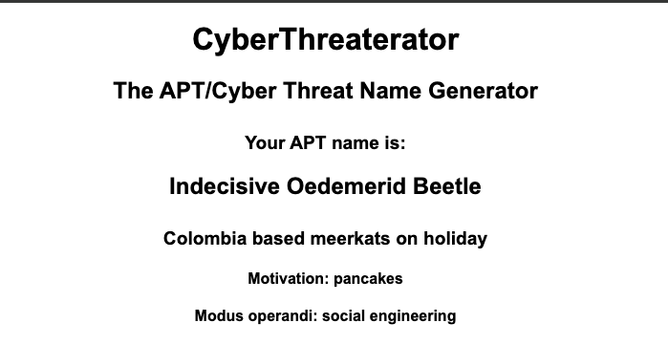
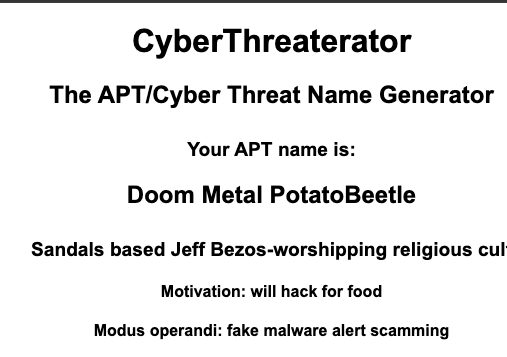
I've made various improvements to CyberThreaterator over lunch breaks, while watching TV, and other non-work brain cycles. There's a plan here: eventually, I want to produce full threat briefs on demand for imaginary actors with IoCs and the rest of what you'd need to protect yourself against them if they were real.
Maybe even a pew-pew map.
 🐀
🐀