| Works at | Sophos |
| Works as | Principal Threat Researcher |
| Non-Infosec things | birds, pottery, shoulder cats, media criticism, natsec |
| https://twitter.com/thepacketrat | |
| blog | https://fancybearfriends.org |
| Work blog | https://news.sophos.com/en-us/author/sean-gallagher/ |
Sean Gallagher  🐀
🐀 
- 4.2K Followers
- 935 Following
- 1,056 Posts
An update on CVE-2025-5777, explaining why orgs should identify systems and patch.
https://doublepulsar.com/citrixbleed-2-electric-boogaloo-cve-2025-5777-c7f5e349d206
Been on radio silence here for a bit. Things are going well. I have finished up the first portion of my onboarding experience at Cisco and am now getting myself up to speed on the ways of Talos threat intelligence. All the people here are awesome. I am stoked.
Also, here’s someone who dropped by today to give me some hints on using Synapse.
Existing
I quit a job recently and started a new one. It was an act of surrender and of hope. Surrender because I had reached a point where I had fought to try to take control of my destiny at a company that, like many others, did not care about my dreams or feelings. Hope because I believed I could still grow somewhere else.
The Garden After the Burn
Another anonymously contributed post from one of our anonymously anonymous authors. Three months ago, I said it was time to admit how bad it’s gotten. I dragged the truth out into the daylight, bruised and blinking, for anyone still willing to look it in the eyes. I named the rot. I pointed at the collapse behind the curtains. I said the quiet part aloud because silence had begun to feel like complicity.
http://thepacketrat.com/2025/06/03/the-garden-after-the-burn/
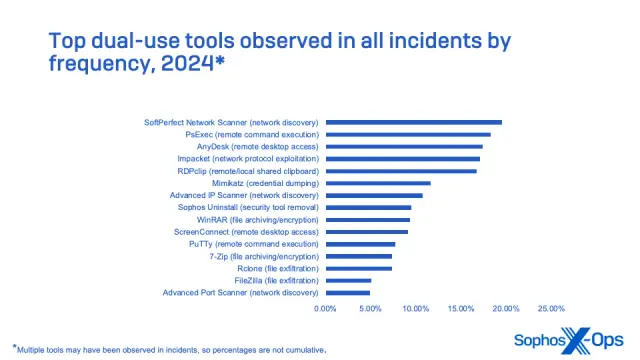
Security Firm @SophosXOps published another report, this one on incidents at small and medium-sized businesses by @thepacketrat and Anna Szalay. One of the things I always look for in these reports are easy #cybersecurity wins -- and this report has a bunch of them.
First off - take a look at this chart: Top 15 dual-use tools. Imagine the pain you can cause threat actors by blocking the use of these tools and disrupting their playbooks!