securefirmware
- 192 Followers
- 114 Following
- 191 Posts
Most known bugs fixed and we are ready for a testing phase before the next EMBA release. Check it out and give us feedback about all the old and new bugs. Your chance to kill our time line ;)
Start with:
git clone https://github.com/e-m-b-a/emba.git
cd emba
sudo ./installer.sh -d
Need some good read for the weekend? Check this ...
Exploring EMBA: Unraveling Firmware Security with Confidence - https://eclypsium.com/blog/exploring-emba-unraveling-firmware-security-with-confidence/
0xFFF: Understanding Unknown Binaries - Firmware Recon - https://www.linkedin.com/pulse/0xfff-understanding-unknown-binaries-firmware-recon-loopglace-vwasf/
Ghosts in the Machine - BruCON 0x0F - https://github.com/n0x08/ConferenceTalks/blob/master/Ghosts%20in%20the%20Machine%20-%20BruCON%200x0F.pdf
Tear Down this Zywall! - https://media.defcon.org/DEF%20CON%2030/DEF%20CON%2030%20presentations/Jay%20Lagorio%20-%20Tear%20Down%20this%20Zywall%20Breaking%20Open%20Zyxel%20Encrypted%20Firmware.pdf
Set-Top Box RE: 6-part series (4 of 6) - https://cc-sw.com/set-top-box-re-6-part-series-4-of-6/
Building on Shaky Ground ISSA - https://github.com/n0x08/ConferenceTalks/blob/master/Building%20on%20Shaky%20Ground_ISSA_SV.pdf
Firmware Guide for Pen Testers - https://eclypsium.com/blog/firmware-guide-for-pen-testers/
Basics of EMBA: A Firmware Analyze Tool for Cybersecurity - https://medium.com/@sansalnuray/basics-of-emba-a-firmware-analyze-tool-for-cybersecurity-e5361773281e
Binary Code Analysis for IEC 62443-4-1 SVV-3 - https://youtu.be/1prqHbTKORU?si=A7qi7MujNjjzTHDA
Have a good time

Exploring EMBA: Unraveling Firmware Security with Confidence - Eclypsium | Supply Chain Security for the Modern Enterprise
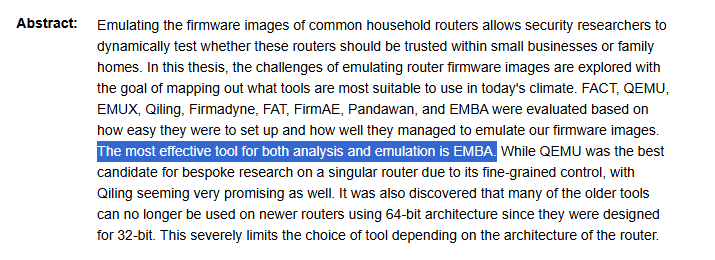
EMBA represents a significant step forward in the realm of firmware security analysis. In a world where our reliance on interconnected devices continues to grow, understanding and securing the firmware supply chain is no longer optional.
The latest EMBA Pull Request for our system emulation engine from our contributor Endri (https://www.linkedin.com/in/endri-hoxha-990b7b239/) is so awesome ...
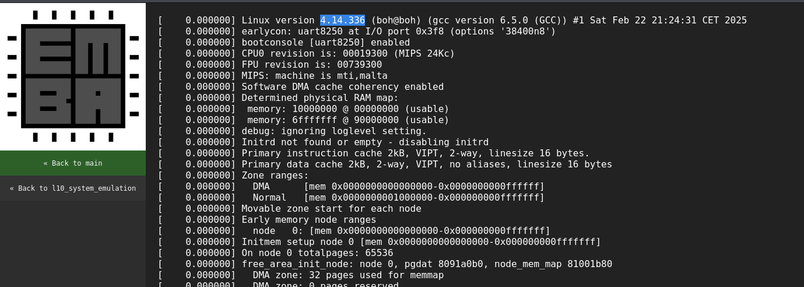
The original Firmadyne/FirmAE kernel that was used in our emulation engine was version 4.1.17 and is from Jan-2016.
The updated EMBA kernel is currently version 4.1.52 from May-2018 (a two year time-travel).
This PR introduces kernel 4.14.336 from Jan-2024 (8 years update from the initial Firmadyne/FirmAE kernel).
Our system emulation engine is now more up to date than ever before. See PR https://github.com/e-m-b-a/emba/pull/1575
Further details about the EMBA emulation engine are available here (updates will follow) https://github.com/e-m-b-a/emba/wiki/System-emulation
@heisec has written a nice article about some vulnerabilities we reported to Siemens in the Sentron PAC1260 device. Check it out here https://www.heise.de/en/news/Root-vulnerabilities-in-Siemens-Sentron-7KT-PAC1260-Data-Manager-remain-open-10350171.html