Yesterday, I presented "Anti-Forensic" techniques for Windows and Linux at the Troopers conference in Heidelberg. This morning at breakfast, I was approached by an attendee and asked if I had looked at the zapper tool from The Hacker's Choice. [1]
I said no, but of course, my interest was piqued 🕵
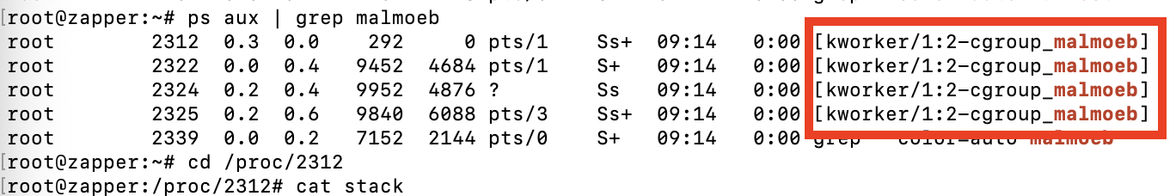
The tool's description on GitHub states: A Linux tool to hide from 'ps'. And that's exactly what it does very well. As in the example from GitHub, I have started a tmux session in my lab, and based solely on the ps output, it is not possible to determine whether tmux is running.
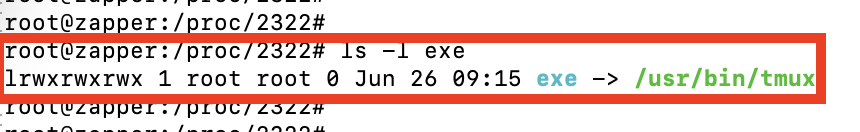
However, /proc to the rescue 🥳. The exe link in one of the (malmoeb) /proc process folders points to tmux, and this way, we could find out relatively quickly what is running behind the process, even if we don't have the command line from the process available.
My team colleague, @hackerkartellet, and I have talked intensively about /proc, available on YouTube. [2]
[1] https://github.com/hackerschoice/zapper
[2] https://www.youtube.com/watch?v=eeYptKewVQ0&t=1s