| We use points / velocity and DO point bugs | |
| We use points / velocity, but do NOT point bugs | |
| We do time estimates and DO estimate bugs | |
| We do time estimates, but do NOT estimate bugs |
Dawn Ahukanna
- 1.7K Followers
- 747 Following
- 10.3K Posts
A gentle introduction to anchor positioning
Anchor positioning allows you to place an element on the page based on where another element is. It makes it easier to create responsive menus and tooltips with less code using only CSS. Here’s how it works.
Source: A gentle introduction to anchor positioning | WebKit
Ironies of Automation, Lisanne Bainbridge, 1983
https://www.complexcognition.co.uk/2021/06/ironies-of-automation.html
“The only way to reconcile that is to drop the quality bar for outputs. But some executives think they’ve found a loophole: put the responsibility for correcting the LLM’s mistakes on the people who are mandated to use that LLM. This is being called “human in the loop” to reassure customers (who also know that AI constantly lies) that the final call is still being made by a qualified professional.”
— @PavelASamsonov
https://productpicnic.beehiiv.com/p/human-in-the-loop-is-a-thought-terminating-cliche
Andrew (@andrewt@mathstodon.xyz)
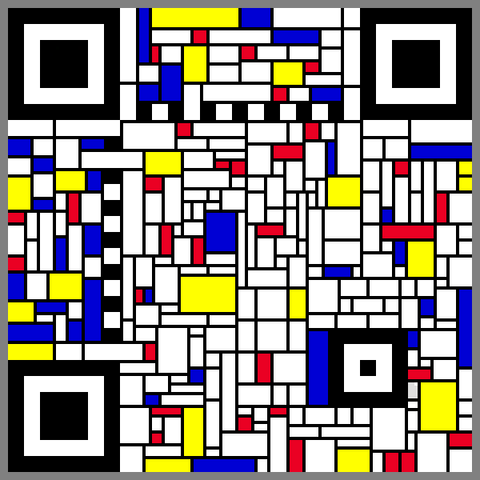
I've put this into a more user-friendly interface so you can make your own silly QR codes. (Watch out, they scan less well than regular QR codes so bear that in mind if you want to use one for anything important. Don't blame me if nobody who gets your flyer can visit your website.) https://www.andrewt.net/dithered-qr-codes/
A working QR code in the style of Piet Mondrian. Inspired @divbyzero and @andrewt.
10 months ago, a company across the world put my neighbor's access to medical care at risk, giving us 2 weeks notice that software behind our 40 electric car chargers would be shut down.
This is the story of how my neighborhood broke free from this potential disaster.
https://natematias.com/portfolio/2025-08-22-unchaining-from-broken-software-tethers/