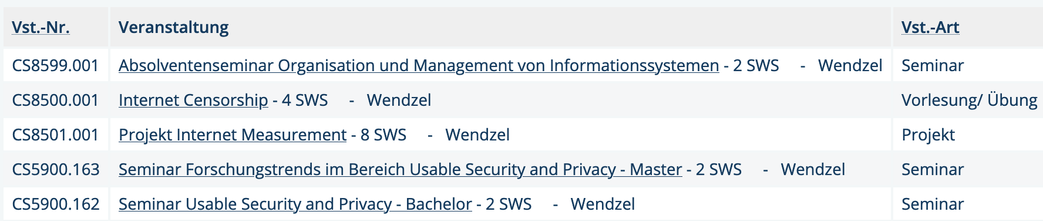
A Generic Taxonomy for #Steganography. Published today by ACM Comp. Surveys (CSUR). Joint-work w/ W. Mazurczyk , @lucacav, A. Mileva, @Jana_Dittmann, @kraetzer, K. Lamshöft, @THB_Security_Research, L. Hartmann, J. Keller, @TN_THB and @niosat
Paper: https://dl.acm.org/doi/10.1145/3729165
#infosec #surveys #taxonomy #informationhiding #covertchannels #stego
There's supplemental material available (just scroll down on the linked page). It also features the description method for steganography techniques.