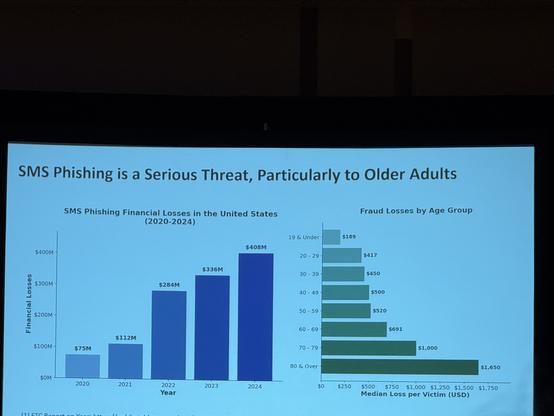
New blog, LLMs as Compilers (1/8)
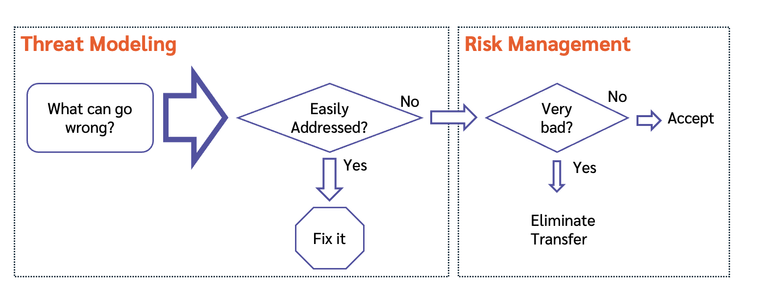
I want to explore the relationship of LLMs to compilers, inspired in part by articles like my AI skeptic friends are all nuts, in part by a lot of time spent exploring LLMs for threat modeling. (There, I feel like I should have more useful things to say before saying them.) And by the way, by “experimenting,” I don’t mean just vibe-threat-modeling (although I’ve done some), but rather carefully constructing prompts, feeding them to multiple engines, scoring the results, and evaluating the evaluations.1 That’s a slow process, but I still feel there’s could be something meaningful, if we can get there. The other inspiration was talking with a friend who builds static analysis tools a very large firm with a famously high bar for developer interviews. He mentioned that people are now checking in their LLM prompts.
Full text: https://is.gd/qh2qKZ