SSD Advisory - Kerio Control Authentication Bypass and RCE - SSD Secure Disclosure
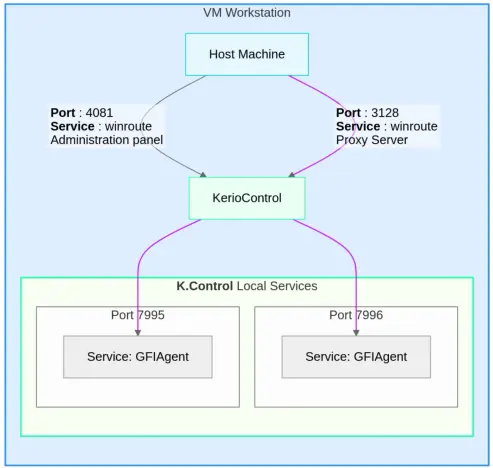
Summary An analysis primarily of Kerio Control revealed a design flaw in the implementation of the communication with GFI AppManager, leading to an authentication bypass vulnerability in the product under audit. Once the authentication bypass is achieved, the attacker can cause the execution of arbitrary code and commands. Credit An independent security researcher, z3er01 of … SSD Advisory – Kerio Control Authentication Bypass and RCE Read More »