Some wild things I found exposed recently that I am actively trying to close down:
1) 🇺🇸 Criminal Defense firm with archived case files exposed (evidence, discovery, court docs, etc) includes crash reports with dead people - Contacted the Law firm last week and nothing done.
2) 🇺🇸 Phone extracts for multiple cases that have been on the news, including a case of a cop suicide, sexual abuse cases - Looking at who to notify about this one, being extra careful as the file listing suggests illegal stuff gathered as evidence might be exposed on it.
3) 🇳🇿 A database backup with a table that includes someone's diary, with a lot of entries about their sexual life.
This backup also includes ~1,500 logins for a police association on other tables and credentials to multiple companies & websites - Contacted higher-ups in the police association for help identifying who is responsible, but so far, no reply.
Just a few more servers to add to the list of dozens of pending cases. Will start escalating contacts until stuff gets fixed.
#cybersecurity #infosec #responsibledisclosure #threatintel #readyouremail

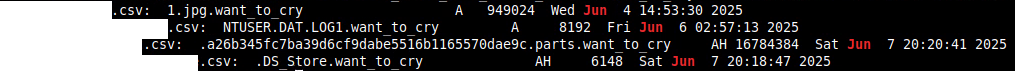
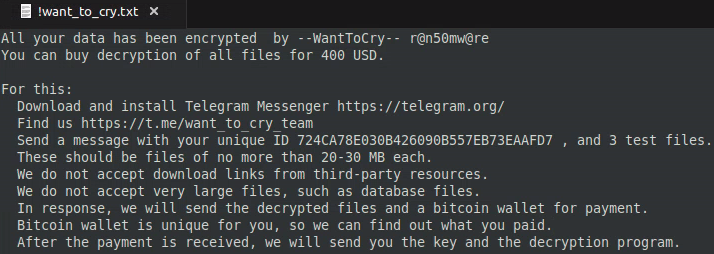
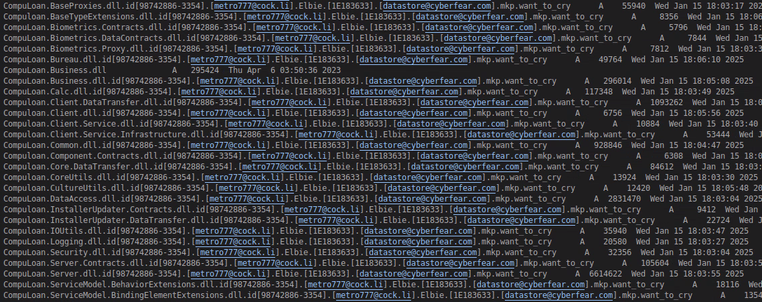
 0 replies to my emails or concerns even though I am 100% sure they were read.
0 replies to my emails or concerns even though I am 100% sure they were read.