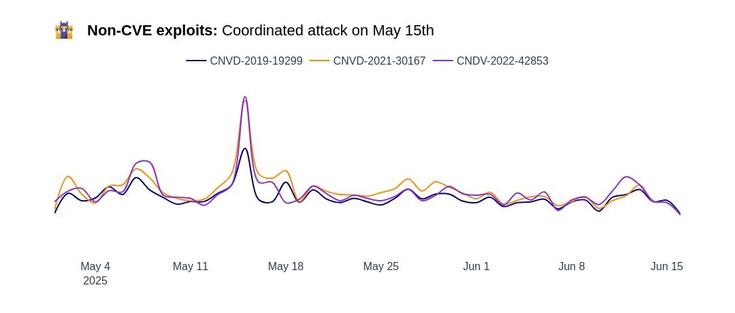
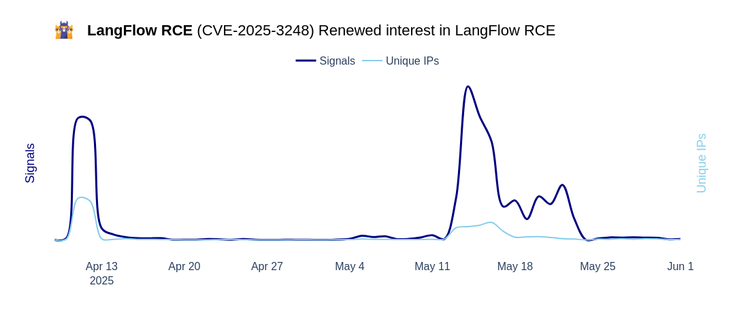
🚨 SAP NetWeaver: Details on a Common Weaponization Timeline
As mentioned in the May CrowdSec VulnTracking report, #SAPNetWeaver (CVE-2025-31324) was a very interesting case study that highlighted the fact that mainstream malicious actors and legitimate security scanners depend on the same PoCs/write-ups to act. Let’s dive into the timeline and key findings.
🔑 Key findings
🔹 Early reports suggest that a select group of highly skilled attackers weaponized the vulnerability before its public disclosure, but mass exploitation began immediately after the exploit details surfaced.
🔹 Common scanning companies were flagged looking for this vulnerability. The first to take action by order of appearance were cert.pl, hadrian.io, and stretchoid, the latter one being still active today and accountable for most of the volume
ℹ️ About the exploit
A critical zero-day vulnerability (CVSS 10.0) was identified in SAP NetWeaver's Visual Composer component. This flaw allows unauthenticated attackers to upload arbitrary files via the /developmentserver/metadatauploader endpoint, leading to remote code execution with high privileges.
🔎 Trend analysis
🔹 First Publish Date (April 24, 2025): Vulnerability disclosed; no public exploits available.
🔹 CrowdSec Network Monitoring Begins (April 26, 2025): No public exploits exist yet, but we deployed a detection rule. Early probes came from advanced actors, 37% used new, disposable infrastructure, while 63% linked to known threats. Alert volume remains very low.
🔹 First Public Exploit (April 29, 2025): Scanning activity skyrockets, nearly 50x the original volume, as public exploits emerge. Both botnets and internet-wide scanners (“the usual suspects” and industry surface management providers) started intensive scanning. At this time, benign actors account for over 50% of scanning activity.
🔹 Following weeks: Slowly, malicious actors decrease in volume of exploitation as they move to other vulnerabilities. Only benign actors remain and account for 90% of the traffic volume.
✅ How to protect your systems
🔹 Patch: Apply SAP Security Note immediately.
🔹 Preemptive blocking: Stay protected in real-time with top-tier blocklists that you can plug in minutes into the most popular security solutions, such as Fortinet.
Sharing insights and taking swift action can collectively reduce the impact of these threats. This is your call to action for real-time threat intelligence and collaborative cybersecurity: https://www.crowdsec.net/integrations
For more information, visit crowdsec.net
Want to stay ahead of the latest cyber threats? Get our weekly Threat Alert Newsletter delivered straight to your inbox, along with critical threat updates and trending cybersecurity insights.
📩 Sign up now for exclusive access: https://contact.crowdsec.net/threat-alert