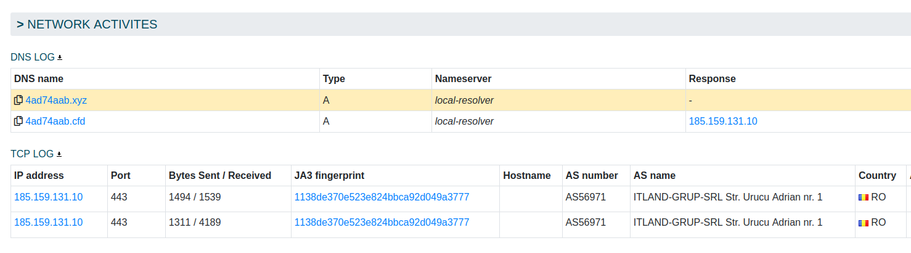
Another #DarkWatchMan campaign began on 15th June, with multiple waves over the following two days 🔥
DarkWatchMan is still written to disk by a .NET dropper. It also uses the same C2 and DGA as the 29th April campaign (the array contains the same initial strings for domains, and the salt for the DGA is also unchanged).
⬇️ Malware sample - initial .NET dropper: https://bazaar.abuse.ch/sample/71857a3bf008c3fae0001470b3405295f95f82a86a2cbb9ff7ed2af1bd6bab90/
📄 Malware sample - DarkWatchMan decoded: https://bazaar.abuse.ch/sample/2830f5f825518188a0e5d1f20d11ceb30b3a8ed4e150cab803f482f1b3f06b46/