Imagine the following situation: your company receives a ZIP file with an invoice, and you're the person responsible for checking if all the details are correct, before sending it off to the payment department. You open the archive, and there's a single PDF inside. You view it, and all the details match—your company's details, seller's company's details, items and total amount are what's expected, and even the bank account number is the same as on previous invoices from this company. As everything looks good, you forward the ZIP with the invoice to the payment team, and move onto reviewing other incoming invoices.
A few days later you receive the same invoice again, but you already have it in the system. Just in case you reach out to the payment department whether it's been paid, and they confirm it has—great, no action required.
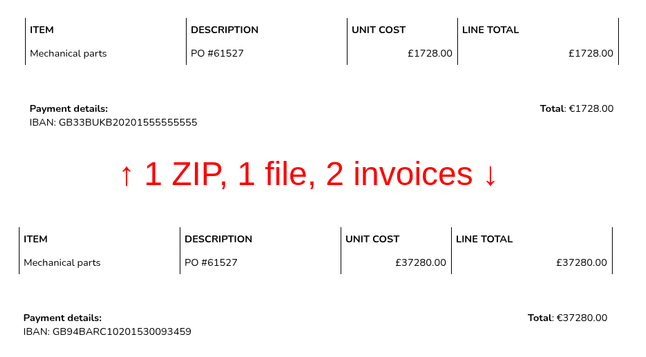
Another month passes by, and you get a "payment due" reminder. What's this? You remember it being paid already, so what gives. You ask the payment team, they again confirm the invoice was settled. You phone the seller about this, but they say they received nothing. So you head down the hall to the payment department, you open the invoice on your laptop, and start going through the details with them. But what's this? The destination account number and amount in the wire transfer and the invoice don't match! The payment team manager's face gets a bit red—seems like it was their mistake? But no! They show you the invoice, and the amount and account number match the actual payment... but it doesn't match what you see on your screen! How can this be?
Both of you re-download the ZIP archive from the email you've forwarded and open the PDF inside. And there it is—you see two different invoices. What in the world is happening?
Immediately you report it up the chain, and your boss's boss gets a pair of IT forensics consultants on the job. They investigate, and later you learn that your company has been scammed with a pair of different invoices hidden inside a schizophrenic ZIP file. This means that you—on your work laptop running a certain software stack—saw and approved the correct invoice. But the payment team—running a different software stack—saw the fake invoice inside the ZIP, which they thought was what you had approved. Even later on you find out that the seller's company has been partially compromised and a lot of their customers got fake invoices. But that's water under the bridge at that point, and the money your company transferred is long gone.
Technical details → https://hackarcana.com/article/yet-another-zip-trick