Vanadium provides a user-facing setting at Privacy and security > WebRTC IP handling policy.
From least to most strict:
Default
Default public and private interfaces
Default public interface only
Disable non-proxied UDP
For Vanadium, "Disabled non-proxied UDP" is the default.
@GrapheneOS so, as someone 100% unfamiliar with android’s internals…
could apps be isolated to different network namespaces a-la linux containers, so localhost to one app isn’t localhost on another app?
@pearl @GrapheneOS https://github.com/GrapheneOS/os-issue-tracker/issues/5225#issuecomment-2799038011
This change would be too large for GrapheneOS to implement it on their own. Especially maintaining such a large feature over time, as updates come out and the underlying network infrastructure in Android changes would require lots of time and effort. It's not feasible for anyone other than Google to implement this.
a sneaky app can detect VPN is on in another profile · Issue #5225 · GrapheneOS/os-issue-tracker
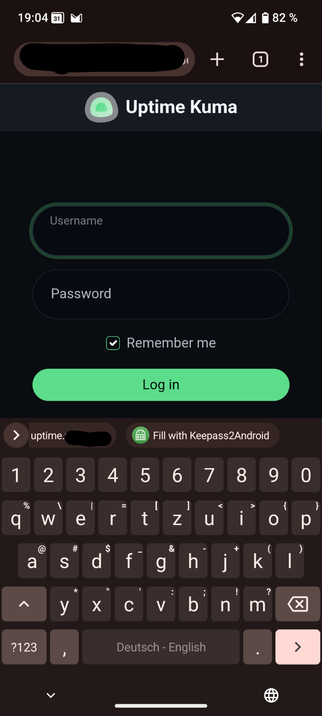
I installed an app in Private Space and it requires me to turn off VPN in Owner Profile in order to log in. I have no VPN in Private Space and the app is not installed in other profiles including O...
@pearl Android does use namespaces to an extent but primarily uses SELinux to make the app sandbox.
It would be possible to use per-profile or per-app network namespaces but it would be very difficult to integrate and maintain in a fully compatible way.
@GrapheneOS So, in theory, updating Vanadium Config could be used to test flags in Alpha such as:
chrome://flags/#strict-origin-isolation
chrome://flags/#origin-keyed-processes-by-default
chrome://flags/#enable-fingerprinting-protection-blocklist-incognito
Note: These are just example flags.
And when you have the Play Services either way, whether you get the app on F-Droid or Play Store, it does not really change much in terms of privacy, but apparently the Play Store might (will?) be more secure.
There are two things i regularly run into when trying to use vanadium:
1. No adblocking/contentblocking (for usability-reasons, not privacy)
2. Missing support for "external" password managers via the autofill service
From what i have read, 1 is a future feature (that i probably can also work around with an adblocking vpn app), and two *should* work. But i am not getting the prompts. Do i need to configure anything special for that?
> 1. No adblocking/contentblocking (for usability-reasons, not privacy)
That's incorrect. Vanadium has content filtering via EasyList + EasyPrivacy with a per-site toggle. It also uses EasyList Germany when German is enabled as a browser language and we plan to extend that to more language lists. This approach is being used to avoid fingerprinting.
> 2. Missing support for "external" password managers via the autofill service
That's incorrect. It fully supports password managers.
@GrapheneOS Oh, you're right! I was looking through the settings and i must have overlooked the 'Ads'-section. That's great! From github issues it looked like it was still experimental.
And i have figured out why the password prompt seemingly does not work. I have been using two-stage logins (ebay/amazon) where it only shows up for the password. Single stage ones seem to work fine. Is this expected, or depends on which password manager i am using?
Sorry for the confusion, and many thanks!
@GrapheneOS @newhinton
Can fully confirm both.
1) Stuff gets filtered but not so much as some would like which is a compromise for fingerprinting not to stand out too much
2) see attached, PWM are working with autofill. KP as autofill service configured and working.
@JeGr @GrapheneOS Thanks, see my other comment. I have overlooked the 'ads' section in the settings which enables/disables adblocking. I wonder if it deserves a more prominent link to it...
Have you had issues with multi-stage logins?
Multi Stage as in? Multiple pages and steps? User, then PW, etc instead of all on one page? Then yes that is sometimes a bit hit or miss and dependent on the form naming etc.
But most times the PW field is fine.
@JeGr @GrapheneOS Yes exactly, multiple pages.
On firefox it works (mostly) as expected, but in vanadium i never got the initial prompt for the username, which put me under the impression it wasn't supported. (And, i remembered that chromium/chrome didn't support autofill at all, but that is probably outdated regardless)
One suggestion, please add user scripts and user agent as it is done in cromite it is also open source
> add user scripts
This is bad for security.
> and user agent
This is bad for privacy and not a good approach to achieving what you probably want to accomplish.
> as it is done in cromite it is also open source
This browser makes many misguided changes and we highly recommend against it. Making more changes does not result in something being better especially when many are done incorrectly or directly significantly reduce security.
Look, I don't really need a user agent, and I use user scripts only to be able to run YouTube or other streaming services in the background when the phone is turned off. Maby you can implement this feature.
And, I think I've seen such a switch in mobile brave browser. In general I would be very glad of a background media playback feature in your browser.
I am a graphene os user and appreciate and support what you are doing.
little ot,
is it possible to show bookmarks
as the Startpage.
just like Vivaldi somehow?
A sync /backup to nextcloud would be nice to.
so or so great³ work!