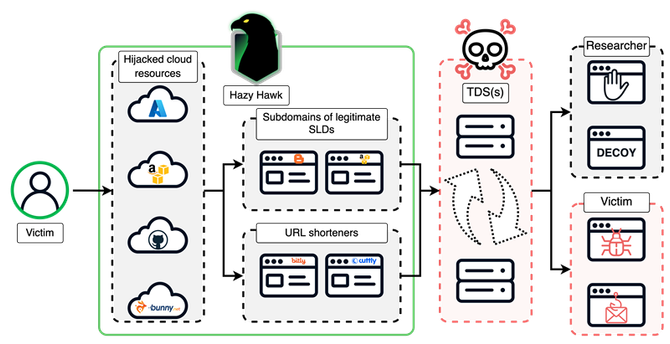
Our latest blog is out! It covers a rising issue that many major organization experiences: Subdomain hijacking through abandoned cloud resources.
This research follows our reporting from earlier in the year about the CDC subdomain hijack. We initially assumed that this was an isolated incident. Well… We were wrong.
We tied some of this activity to a threat actor, dubbed Hazy Hawk, who hijacks high-profile subdomains which they use to conduct large-scale scams and malware distribution.
https://blogs.infoblox.com/threat-intelligence/cloudy-with-a-chance-of-hijacking-forgotten-dns-records-enable-scam-actor/
#dns #threatintel #threatintelligence #cybercrime #cybersecurity #infosec #infoblox #infobloxthreatintel #scam #HazyHawk