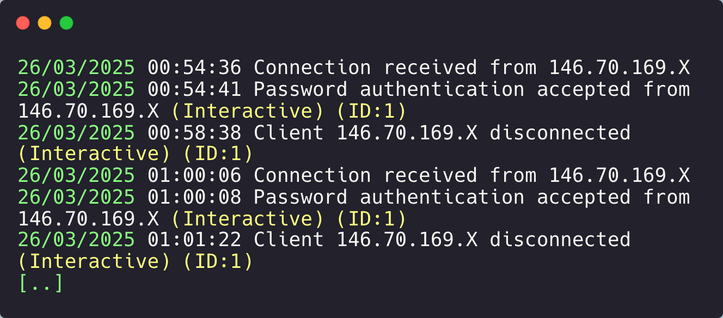
An attacker installed UltraVNC as a backdoor on a domain controller during a recent incident response engagement. During our analysis, we found that the attacker logged in from an IP address belonging to M247 (see image).
Many of these RMM tools (and file transfer tools, too) are generating log files that we can leverage in our investigations. Here is the relevant log file for UltraVNC:
C:\ProgramData\Packages\uvnc bvba\UltraVNC\mslogon.log
JPCERT has published a very good and detailed presentation with more artifacts and information:
https://jsac.jpcert.or.jp/archive/2023/pdf/JSAC2023_1_1_yamashige-nakatani-tanaka_en.pdf