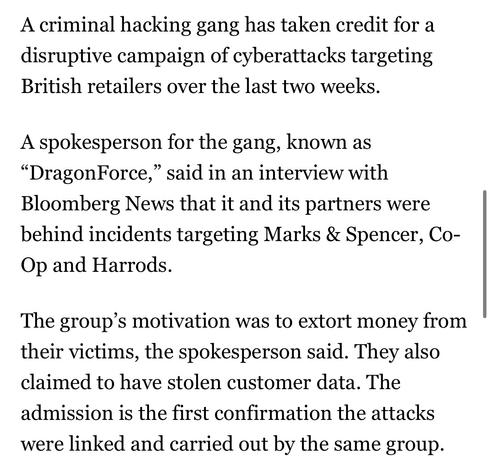
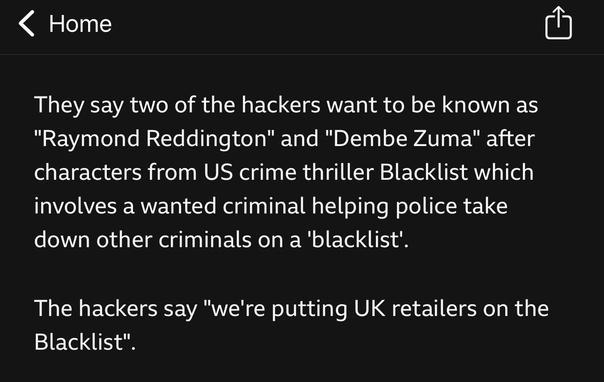
DragonForce Ransomware Cartel are claiming credit for attacks on Marks and Spencer, Co-op and Harrods and say more victim orgs are coming https://www.bloomberg.com/news/articles/2025-05-02/-dragonforce-hacking-gang-takes-credit-for-uk-retail-attacks
I'm going to make this the new ongoing megathread for DragonForce Ransomware Cartel's attack on UK retailers as they're all connected.
Why it matters: these are some of the UK's largest retailers, think Target or some such in a US sense.
Prior threads
M&S: https://cyberplace.social/@GossiTheDog/114381946765071799
Co-op: https://cyberplace.social/@GossiTheDog/114426688834113446
Harrods:
https://cyberplace.social/@GossiTheDog/114433519351165250
The individuals operating under the DragonForce banner are using social engineering for entry.
Defenders should urgently make sure they have read the CISA briefs on Scattered Spider and LAPSUS$ as it's a repeat of the 2022-2023 activity.
Links: https://www.cisa.gov/sites/default/files/2023-08/CSRB_Lapsus%24_508c.pdf
https://www.cisa.gov/sites/default/files/2023-11/aa23-320a_scattered_spider_0.pdf
I would also suggest these NCSC guides on incident management: https://www.ncsc.gov.uk/collection/incident-management
and effective cyber crisis comms: https://www.ncsc.gov.uk/guidance/effective-communications-in-a-cyber-incident
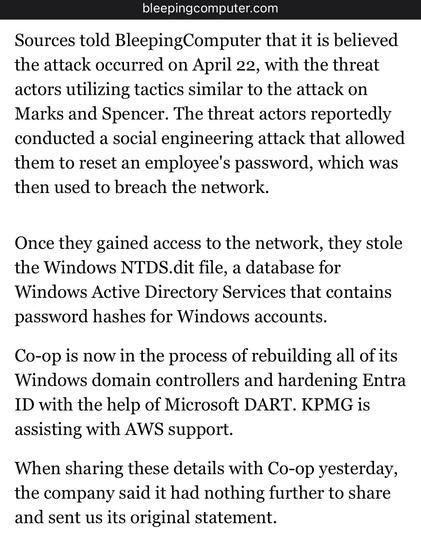
Co-op Group have now admitted a significant amount of member (customer) information has been stolen by DragonForce Ransomware Cartel, saying they "accessed data relating to a significant number of our current and past members" - around 20 million people. The Membership database, basically. That includes home addresses and phone numbers etc.
Up until now Co-op hadn't even used the words cyber or threat actor, referring to an "IT issue" and "third party" in comms.
New by me - breaking down the attacks on UK highstreet retailers
Regarding IOCs around the UK retailer activity - there’s loads doing the rounds, and they’re almost all not useful.
Eg hundreds of dynamic VPN IPs from 2022. If you google them you’ll find them on vendor blogs from years ago for Scattered Spider - people are recycling in panic and passing around in panic.
Don’t hunt on random IOCs. IP addresses change. Strengthen foundational controls. Review sign in logs for abnormal activity etc.
Bleeping Computer have more on the Co-op breach https://www.bleepingcomputer.com/news/security/co-op-confirms-data-theft-after-dragonforce-ransomware-claims-attack/
One of M&S’ biggest suppliers have said they have reverted to pen and paper for orders due to M&S lacking IT.
Additionally, M&S staff are raising concern about how they will be paid due to lack of IT systems.
M&S are over a week into a ransomware incident and still don’t have their online store working.
Here's the ITV News report anyhoo, logline: "ITV News understands the the ongoing cyberattack faced by the supermarket has worsened since Friday, impacting the ordering system, drivers and warehouse staff."
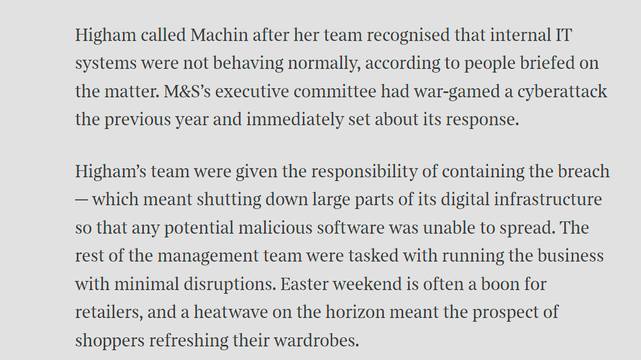
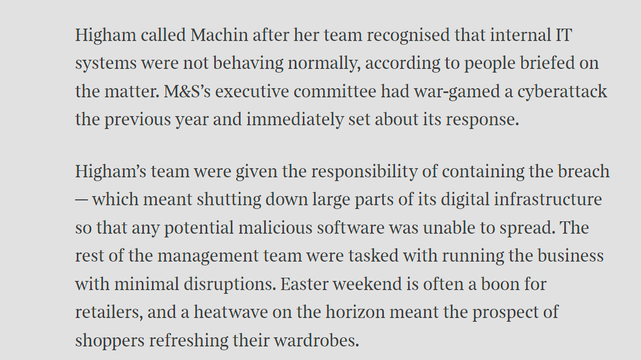
Sunday Times has a piece looking into ransomware incident at Marks and Spencer. It's pretty good, goes into their contain and eradicate focus.
"By shutting down parts of the IT estate, Higham’s team had worked to prevent the attack from spreading, but had also stopped parts of its digital operations from functioning. This was considered a worthy trade-off."
One error in the article - lack of recovery doesn't mean no ransomware paid. Paying is not quick restoration.
https://www.thetimes.com/business-money/companies/article/m-and-s-cyber-attack-ms-klrnxvwq6
Great NCSC piece by @ollie_whitehouse
I’d add - block by Entra policy specifically High risk logins (below is too FP prone), and SOC monitor them. SOC playbook = account probably compromised. How?
https://www.ncsc.gov.uk/blog-post/incidents-impacting-retailers
Sky News quote a source in M&S head office saying Marks and Spencer have no ransomware incident plan so they are making it up as they go along apparently, with staff sleeping in the office and communicating via WhatsApp.
M&S dispute this, saying they have robust business continuity plans.
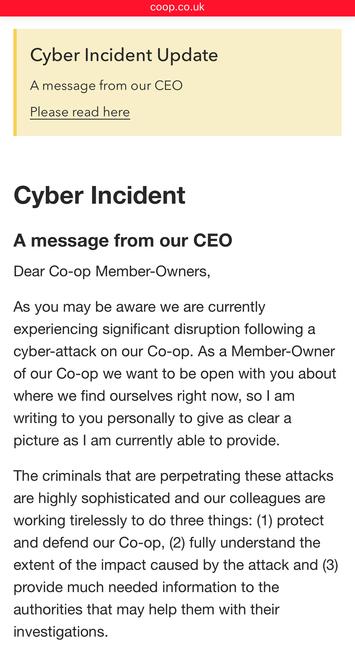
Co-op Group appear to be trying to course correct with their cyber incident comms.
They’re calling it a cyber incident now, and have put a statement on the front page of their website, along with an FAQ. They haven’t yet emailed members (they should). Edit: they’ve started emailing members.
@mjr @GossiTheDog If its an ATM inside the store, then the issues with Co-op should have no/little impact.
Those ATMs are very segregated on retailer's networks and really the retailer does nothing except provide connectivity.
In essence, unless the retailer has a MASSIVE connectivity issue, those cash machines will keep work (that is, until they run out of money to actually dispense - that's the real risk of what will happen).