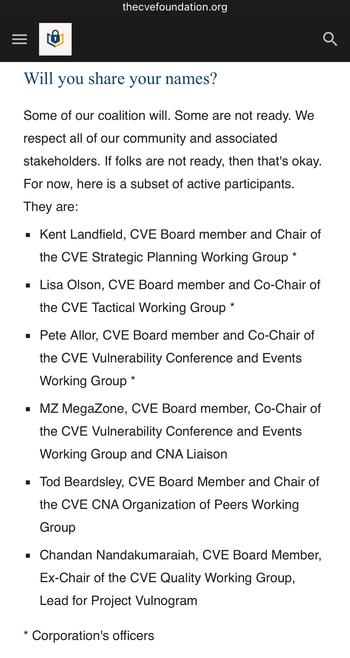
@acalarch @GossiTheDog Most of the people involved have 'day jobs' and not all employers are necessarily supportive. Some people asked to have time to first discuss what's happening with their employer before their name is public.
Especially as we're already seeing people presume that because someone involved with the Foundation works for Employer X it must mean Employer X is backing the Foundation - which is not safe to assume. So there is some concern about blowback on employers causing problems for the individual.
People are participating as individuals, not corporate representatives. As people are comfortable being named they'll be added to the FAQ entry.
(This is MegaZone. F5 is not officially involved, but supports employees working on initiatives outside of F5. They're aware of what I'm doing - our CEO commented on my LinkedIn post about being part of this.)