Now sharing open IP tunnel hosts in a new daily Open IP-Tunnel report https://shadowserver.org/what-we-do/network-reporting/open-ip-tunnel-report/
These hosts accept tunnelling packets such as IPIP, GRE without authenticating the source IPv4 or IPv6 addr, which can be abused for DoS/other attacks
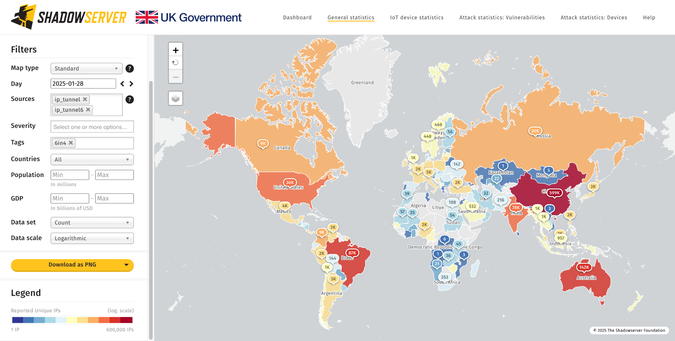
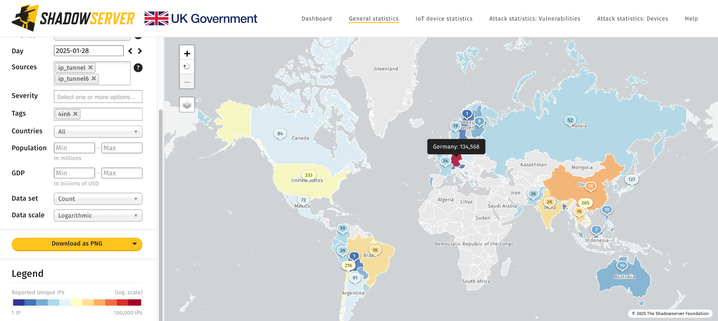
~436K GRE & ~66K IPIP vulnerable IPs found on 2025-01-14
Geo breakdown (GRE/GRE6):
Geo breakdown (IPIP/IP6IP6):
These vulnerabilities were discovered by Angelos Beitis and Mathy Vanhoef @vanhoefm at the DistriNet Reseach Unit at KU Leuven University in Belgium. Thank you for the collaboration!
You can find more details on the vulnerabilities at: https://github.com/vanhoefm/tunneltester
MEDIUM: Open IP-Tunnel Report | The Shadowserver Foundation
DESCRIPTION LAST UPDATED: 2025-01-28 DEFAULT SECURITY LEVEL: MEDIUM This report contains information about a vulnerability that allows new Denial-of-Service (DoS) vulnerabilities. This vulnerability originates from hosts that accept tunnelling packets such as IPIP, GRE, 6in4 and 4in6 without authenticating the source IPv4 or IPv6 address. Attackers can exploit these hosts as proxies to conceal their […]