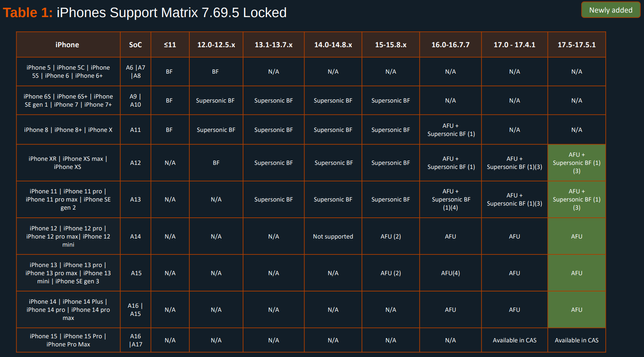
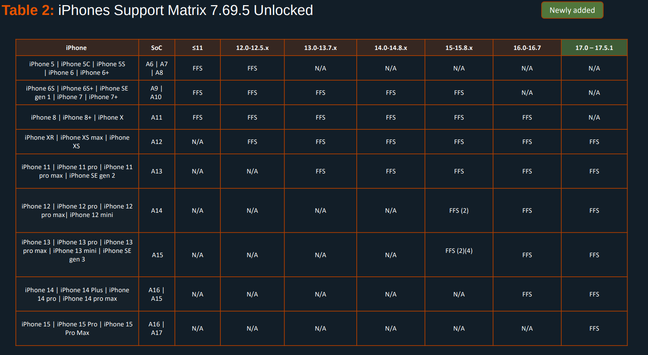
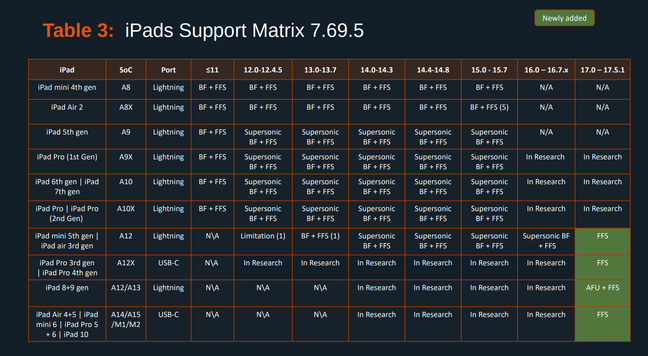
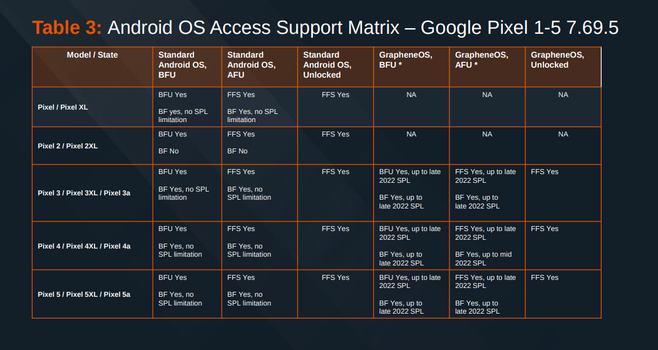
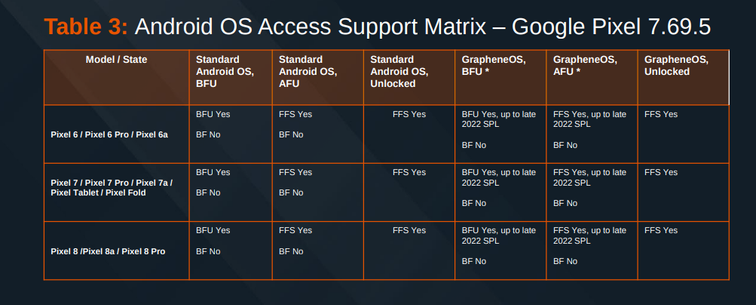
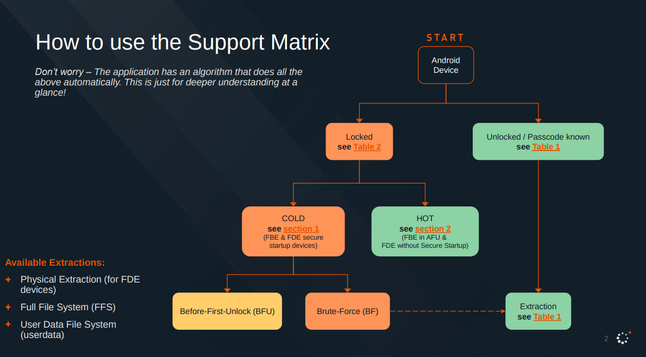
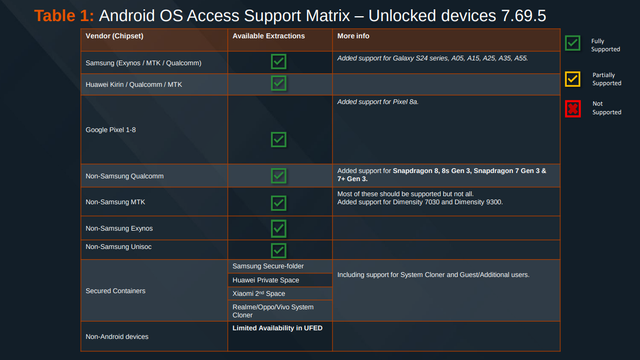
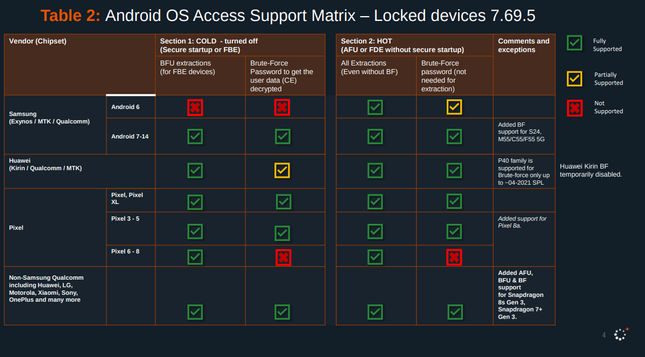
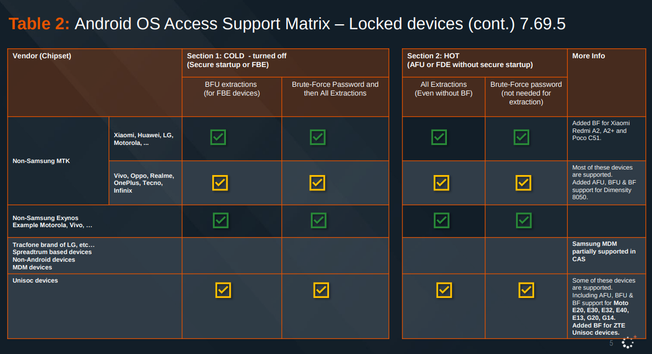
Here's the Cellebrite Premium 7.69.5 iOS Support Matrix from July 2024.
404media recently published an article based on the same April 2024 docs we received in April and published in May. Many tech news sites including 9to5Mac made incorrect assumptions treating that as current.