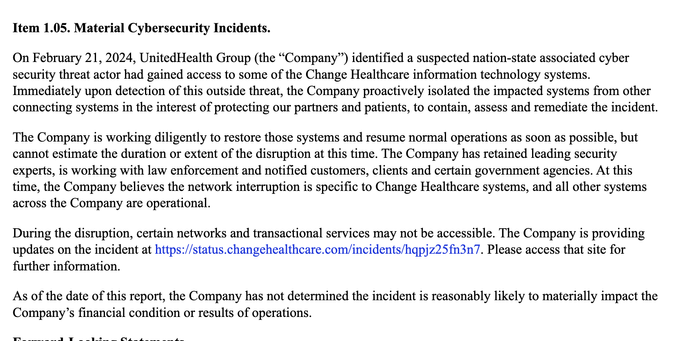
As spotted by @zackwhittaker, Change Healthcare outage (still ongoing) is listed as suspected nation state threat actor in their 8-K filing.
In my experience it’s *extremely* rare to isolate the whole production network for nation state and espionage.. I don’t know what happened to trigger that here.
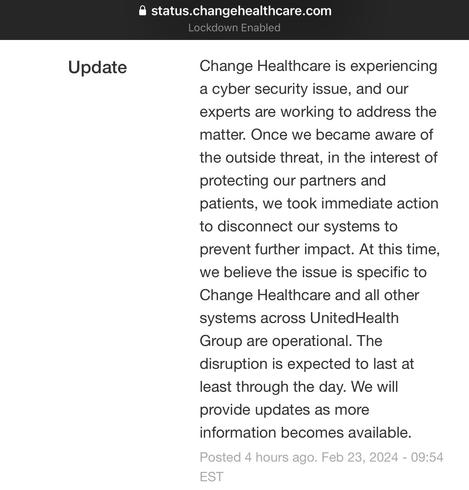
It’s over 48 hours since the Change Healthcare outage over a “cyber security issue” began.
I have heard they may have been deliberately wiped.
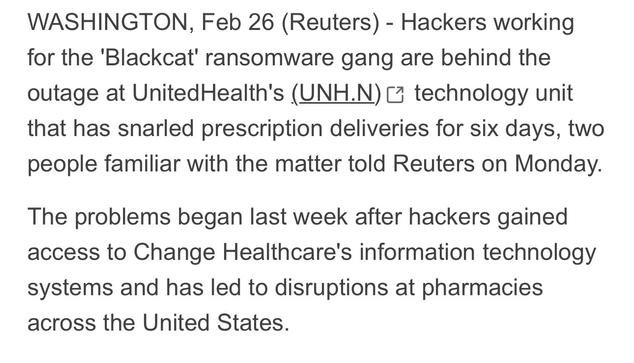
Reuters reports the Change Healthcare outage, which is still ongoing almost a week later, was not caused by a “nation state” as claimed by the victim - but it’s an AlphV ransomware incident. https://www.reuters.com/technology/cybersecurity/cyber-security-outage-change-healthcare-continues-sixth-straight-day-2024-02-26/
The Change Healthcare incident is rumbling on. They’ve now acknowledged it is AlphV ransomware group, not a nation state as they prior claimed. https://techcrunch.com/2024/02/29/unitedhealth-change-healthcare-ransomware-alphv-blackcat-pharmacy-outages/
Since the Change Healthcare ransomware incident started several weeks ago, they've had a status page saying the incident will continue for 'the next day'.
Their COO has privately briefed orgs that will be "weeks" longer.
HT @brett for link
https://www.statnews.com/2024/02/29/change-healthcare-cyber-attack-outage-will-last-for-weeks/
AlphV ransomware group has received a $22m ransom payment, reportedly from Change Healthcare.
Rumours are AlphV has now scammed the ransomware affiliate and Change Healthcare, by stealing the ransom and exit scamming.
Downstream hospitals say they are losing around $100m a week due to the ongoing service outage.
https://www.wired.com/story/alphv-change-healthcare-ransomware-payment/
Some good reporting here - the NCA, who are listed on the AlphV portal as being involved in a takedown - say they were not involved in a takedown.
We’ll see what the FBI says, but it looks like AlphV may well have done rug pull aka exit scam — stole their operator and affiliate’s money and left their victims without decryption.
For anybody wondering on the financial impact of the ongoing Change Healthcare ransomware incident (yes, obviously there’s also a big patient impact too):
https://therecord.media/cash-flow-disruptions-hospitals-change-healthcare
The bad news is I think ransomware groups will cause much bigger problems further down the line as they’re basically teenagers with rocket launchers inside critical infrastructure, blindly firing. They know governments worldwide are impotent.
$100 million a day? Cash flow disruptions roil healthcare industry after cyberattack
The economic impact of the Change Healthcare cyberattack continues to come into focus, with experts saying some large industry players — such as hospital and pharmacy networks — are facing disruptions costing upwards of $100 million a day.
International law enforcement all deny being behind the claimed AlphV takedown. So, exit scam confirmed.
One victim org has reached out to me asking how they contact AlphV as they still need to pay as part of claiming insurance. 💀
https://therecord.media/europol-doj-nca-deny-involvement-in-alphv-blackcat-ransomware-takedown
Europol, DOJ, NCA deny involvement in recent AlphV/BlackCat ‘shutdown’
Several of the law enforcement agencies involved in the takedown of one of the most prolific ransomware groups denied involvement in a new notice posted to the gang’s leak site — adding weight behind rumors from experts and cybercriminals that the group was attempting to carry out an elaborate exit scam.
At least 5 lawsuits have been filed over the Change Healthcare ransomware incident so far.
https://www.hipaajournal.com/multiple-class-action-lawsuits-change-healthcare-ransomware-attack/
Here's one of the court documents: https://www.scribd.com/document/711110045/UnitedHealth-Change-Health-proposed-class-action-lawsuit
The Change Heathcare ransomware incident is still going and is having profound implications for people and the healthcare industry across the US.
But for people who think this is an isolated incident, it isn’t - it’s been like this for several years where civil society is gradually being eroded by some gangs of often kids, from schools to councils to public services worldwide (except, er, Russia).
https://prospect.org/health/2024-03-11-change-unitedhealth-ransomware-pharmacies/
HT to @zackwhittaker, the US department of health has opened an investigation into Change Healthcare around if data exfiltration occurred.
It’s typically very easy to find out if data exfil happened as a third party as you can see large volumes of data transfer to VPS providers or cloud storage providers in ISP logs (which are sold onwards).
The Change Healthcare ransomware situation is still going on, almost a month later, with at least one downstream healthcare provider saying they have run out of money to pay staff. https://www.berkshireeagle.com/news/local/cyberattack-change-healthcare-united-ransomware-medical-insurance-payments-berkshire-allergy-care/article_a5547ef2-e302-11ee-9162-2b0ff10b145f.html
HT @brett
A major cyberattack has caused a Pittsfield medical practice to run out of money. Staff are continuing to treat patients
“After this week’s payroll, we’re going to be broke.” Dr. Thomas B. Edwards of Berkshire Allergy Care on South Street, speaking of the cyberattack that has rattled doctors' offices around
One of the largest nursing home operators in the U.S. has filed for bankruptcy citing the ongoing Change Healthcare ransomware incident as a cause.
They also got hit with ransomware themselves a few months prior.
The US government are offering $10m for information on the AlphV ransomware operator who attacked Change Healthcare https://www.reuters.com/technology/cybersecurity/us-offers-10-million-bounty-info-blackcat-hackers-who-hit-unitedhealth-2024-03-27/
Worth noting that when the incident began, the company involved refused to say #ransomware and instead claimed it was a nation state attack.
Ransomhub have provided Wired journalists with files from Change Healthcare - meaning they’re being held to ransom again. https://www.wired.com/story/change-healthcare-ransomhub-threat/
Change Healthcare have told investors they have so far taken a $872 million hit in dealing with their ongoing ransomware incident in the first two months, with the cost expected to rise to between $1350m-$1600m through the calendar year.
Shareholders don't appear to care as the stock is up 5% since the update.
https://www.theregister.com/2024/04/16/change_healthcares_ransomware_attack_has/
Wall Street Journal has a leak from the Change Healthcare ransomware incident
- Initial entry was via a remote access system without MFA
- Dwell time was 9 days
- They paid the ransom, then got held to ransom again and had data leaked anyway
UnitedHealth says Change Healthcare ransomware threat actor stole health data on ‘substantial proportion of people in America’
Change Healthcare deal with the healthcare information of around half of Americans. https://techcrunch.com/2024/04/22/unitedhealth-change-healthcare-hackers-substantial-proportion-americans/ #threatintel #ransomware
The CEO says entry to Change Healthcare was via an unspecified Citrix vulnerability https://www.reuters.com/technology/cybersecurity/unitedhealth-hackers-took-advantage-citrix-vulnerabilty-break-ceo-says-2024-04-29/
This conflicts with a prior WSJ report saying lack of MFA. Although maybe lack of MFA on Netscaler was the vulnerability.
TechCrunch has really good coverage: https://techcrunch.com/2024/04/30/uhg-change-healthcare-ransomware-compromised-credentials-mfa/
Change Healthcare didn’t use MFA on Citrix Netscaler. It was a bog standard ransomware incident.
One learning for the industry btw - I saw loads of threat intel channels circulating incorrect info about the incident. That’s fine, but some (eg the health info sharing authorities) reshared this wrong info.
The CEO of UnitedHealth is due to give testimony in Washington on their Change Healthcare ransomware incident tomorrow, where he will say “Our company alone repels an attempted intrusion every 70 seconds – thwarting more than 450,000 intrusions per year”
That sound impressive, but if you own a Windows PC at home, you’re doing the same thing - it’s called the built in firewall.
Not having MFA on Citrix Netscaler is also called negligence.
Change Healthcare say their data breach, caused by their lack of MFA on Citrix Netscaler and AlphV ransomware group, impacted 100m Americans, making it the largest healthcare breach to date. https://www.reuters.com/technology/cybersecurity/hack-unitedhealths-tech-unit-impacted-100-mln-people-2024-10-24/
@GossiTheDog “Not having MFA on Citrix Netscaler “
OhNo
@GossiTheDog I was pretty sure we didn’t have that option when I was still an admin, so I checked… Netscaler added MFA support in NetScaler 12.1 build 51.16, which was released March 28, 2019.
I would say five years is plenty of time to implement.
@GossiTheDog When we developed our SOC, we decided to omit this bullshit number in our reports. This the white noise.
More important to the management to know is the number and quality of unfixed problems.
@GossiTheDog My Windows firewall on my PC at home does not see any external attacks whatsoever.
Hint: The PC is behind a NAT router.
@GossiTheDog I know that I keep saying this, but people need to go to jail for this.
UnitedHealth should not be handling 1/3rd of the entire countries health records. Who the fuck approved of this?
Their malfeasance is causing tangible, physical, harm to the country. People have absolutely died or been hurt by not being able to get their prescriptions.