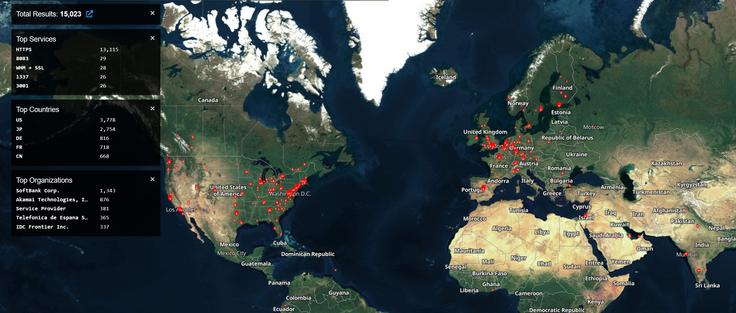
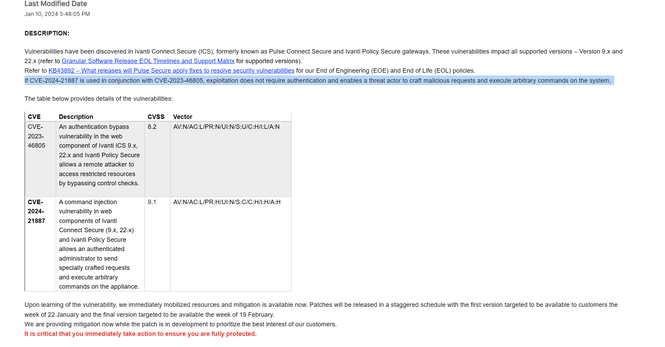
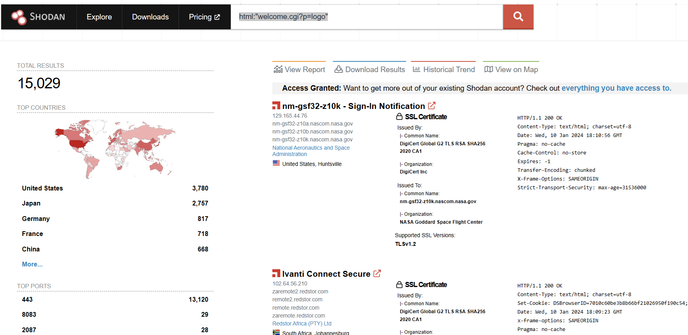
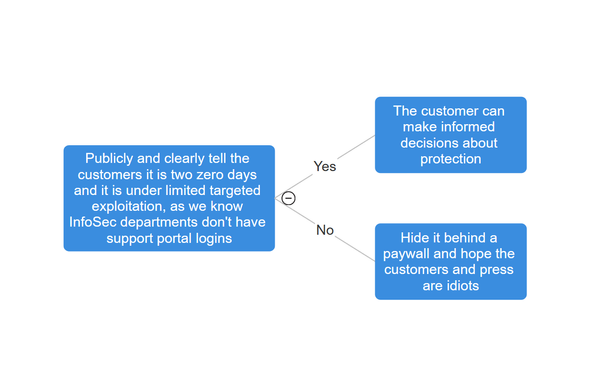
⚠️ want a highly impactful, actively exploited border gateway zero days situation to wake you up?
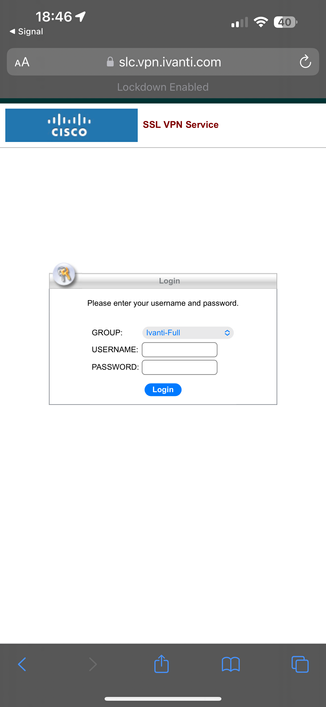
Ivanti Pulse Secure aka Ivanti Connect Secure and Ivanti Policy Secure Gateway customers - prepare to deploy mitigations and await follow on patches.
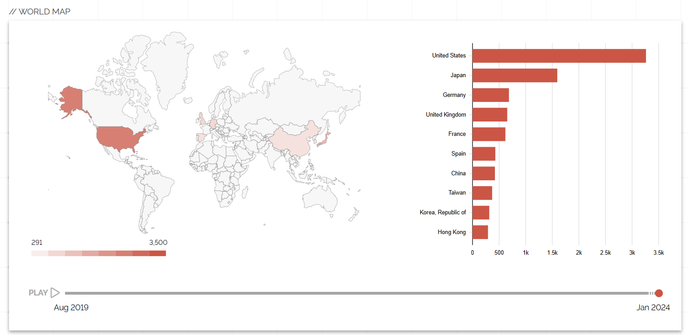
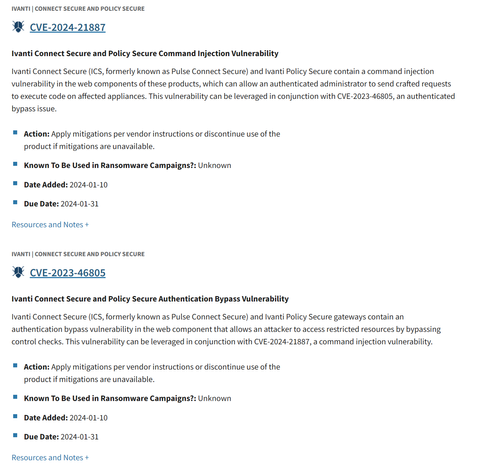
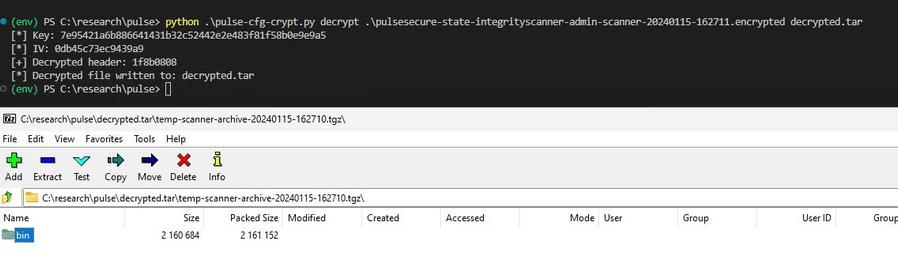
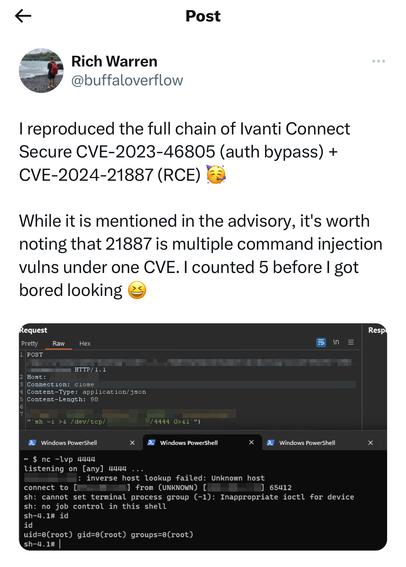
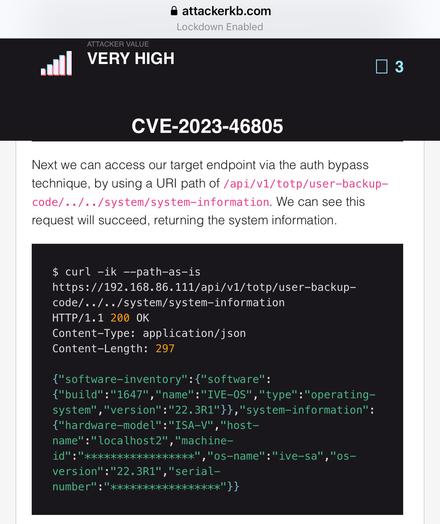
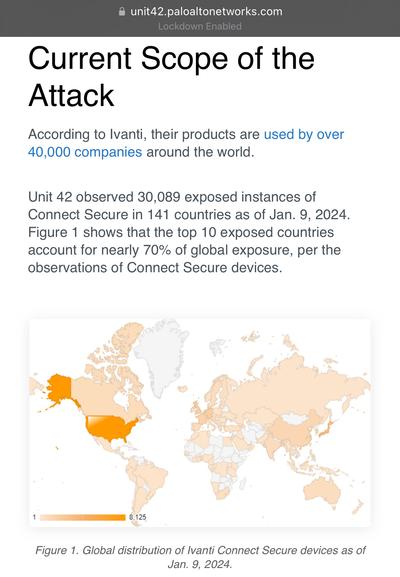
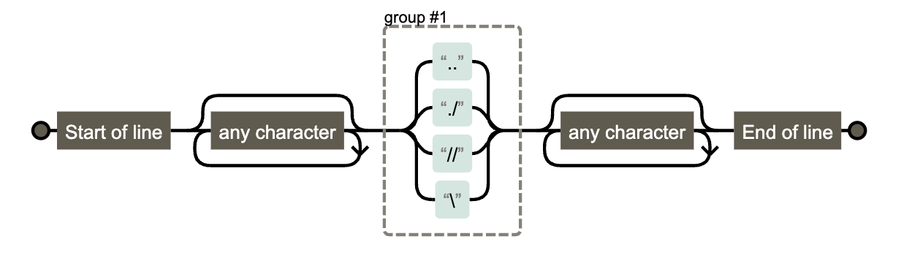
In the wild exploitation, probable nation state - includes authentication (including MFA) bypass and code execution.
Looks like Ivanti have done a really good job identifying.
I call it ConnectAround. #threatintel #connectaround