#HashiCorp #consul #ConsulProject
#HashiCorp #consul #ConsulProject
#bitBlog Managing dynamic secrets with #Hashicorp Vault & Boundary
https://blog.bitexpert.de/blog/dynamic_secrets_with_vault_boundary
Just wrapped up our live session where we dove into setting up HashiCorp Consul policies!Missed it? Catch the VOD on our channel and stay tuned for more DevOps deep dives.
Follow @theDevCastOps for more live infra and cloud-native content!
Dear #AWX users out there (AWX as in Ansible, not AWS as in Amazon...),
does anyone have good pointers on connecting AWX and #Hashicorp #Vault / #OpenBoa **without** having to define each secret/credential again in AWX?
I have set up a basic connection according to the documentation: https://ansible.readthedocs.io/projects/awx/en/24.6.1/userguide/credential_plugins.html#ug-credentials-hashivault
And I have created a credential using that lookup and could successfully output its value in a playbook run in AWX.
But having to define a AWX credential for each secret that I need to pull from Vault/OpenBoa sounds like a lot of unnecessary duplication.
(Yes, I know you can manage AWX via Ansible. We do that already. But still, you need to define the credentials in your code somewhere for the automation to create it in AWX)
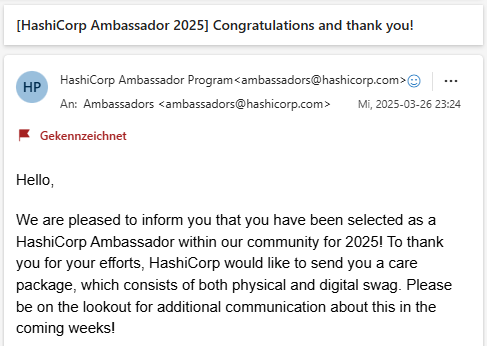
🚀 Excited to share that I’ve been selected as a HashiCorp Ambassador! 🏅
Honored to join a global community of cloud innovators & contribute through content, mentoring, & collaboration.
Let’s build scalable, secure systems! 🌍🔧
I'm excited to announce that I've been selected as a HashiCorp Ambassador for 2025.
Our journey with HashiCorp started early on with Vagrant to simplify project virtualization. In 2019, we chose Nomad over Kubernetes for its simplicity and scalability. Last year, we implemented Boundary & Vault for simple and secure remote access based on user identity.
If you want to know more about Nomad or Boundary, let me know.
Uuuuuuuh, #OpenBao (the open source fork of #Hashicorp #Vault) just released version 2.2.0 and now includes the UI, that was missing so far.
The package for @opensuse was adapted, tested and worked out fine. Will soon be available in #Tumbleweed!
If you want to test this out, feel free to use this vagrant-libvirt setup of mine:
https://codeberg.org/johanneskastl/openbao_vagrant_libvirt_ansible
#openSUSE #secretsmanagement #opensource #hellyeah #vagrant #libvirt