https://hhj4ck.github.io/qualcomm/2025/08/06/secboot-off-qcm2150.html
You
- 138 Followers
- 840 Following
- 110 Posts
https://hhj4ck.github.io/qualcomm/2025/08/06/secboot-off-qcm2150.html
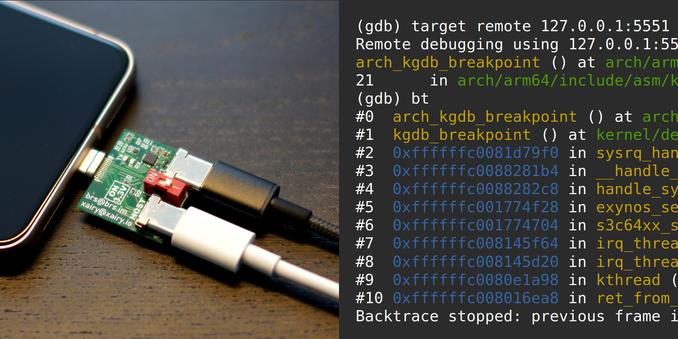
Documented instructions for setting up KGDB on Pixel 8.
Including getting kernel log over UART via USB-Cereal, building/flashing custom kernel, breaking into KGDB via /proc/sysrq-trigger or by sending SysRq-G over serial, dealing with watchdogs, etc.
https://medium.com/@lighthousereports/using-leaked-data-to-examine-vulnerabilities-in-sms-routing-and-ss7-signalling-8e30298491d9
Really interested in seeing what new avenues this opens for threat hunting.
https://letsencrypt.org/2025/07/01/issuing-our-first-ip-address-certificate/

We've Issued Our First IP Address Certificate
Since Let’s Encrypt started issuing certificates in 2015, people have repeatedly requested the ability to get certificates for IP addresses, an option that only a few certificate authorities have offered. Until now, they’ve had to look elsewhere, because we haven’t provided that feature. Today, we’ve issued our first certificate for an IP address, as we announced we would in January. As with other new certificate features on our engineering roadmap, we’ll now start gradually rolling out this option to more and more of our subscribers.
Link: https://github.com/jackjackbits/bitchat
Comments: https://news.ycombinator.com/item?id=44485342
Unveiled at #TROOPERS25 - Hexagon fuzzing unlocked
Hexagon is the architecture in Qualcomm basebands - they power most of the world's leading smartphones.
Until now, this baseband was out of reach.
We released the first open-source toolchain for system-mode Hexagon fuzzing, presented by Luca Glockow (@luglo), Rachna Shriwas, and Bruno Produit (@bruno) at @WEareTROOPERS
Full post: https://www.srlabs.de/blog-post/hexagon-fuzz-full-system-emulated-fuzzing-of-qualcomm-basebands
How we opened up mobile firmware in 3 steps:
1. Boot real iPhone basebands with a custom QEMU fork
2. Rust-powered fuzzer controls execution via JSON configs
3. Ghidra integration maps coverage across threads
This brings full visibility to Qualcomm’s 4G/5G/GPS stacks.
Reproducible. Extendable. Open source.
Hexagon’s no longer off-limits - mobile security just got a lot more transparent.
🔗 Try it yourself: https://github.com/srlabs/hexagon_fuzz
📚 Docs: https://github.com/srlabs/hexagon_fuzz/blob/main/docs/reverse_engineering.md
🖥️ Slides from Troopers25: https://github.com/srlabs/hexagon_fuzz/blob/main/docs/talk/hexagon_fuzz_troopers2025.pdf
🛠️ Issues, ideas, or contributions? PRs welcome.
Link: https://www.linaro.org/blog/hidden-jtag-qualcomm-snapdragon-usb/
Comments: https://news.ycombinator.com/item?id=44426428