Xeno Kovah
- 128 Followers
- 9 Following
- 106 Posts
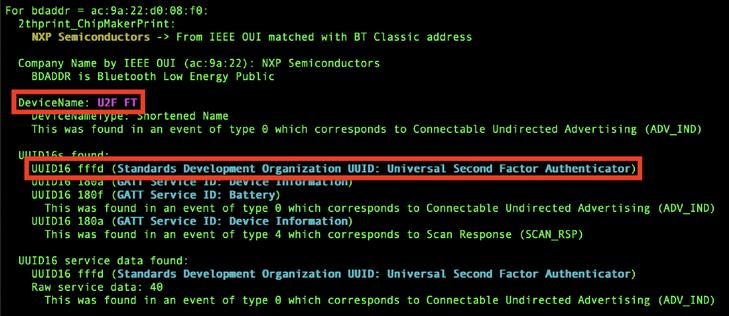
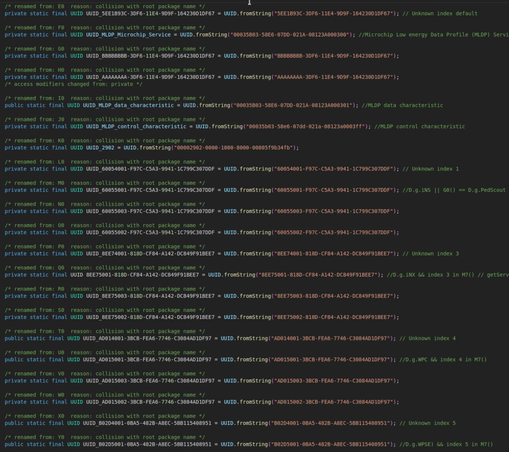
Those "hacked" crosswalk buttons last week were most likely just things that hadn't changed the default password (from "1234"), and then someone used the Polara app to upload new audio (which is part of its core functionality.) Today I decompiled the Android app and added the UUIDs (pic1) to CLUES: https://github.com/darkmentorllc/CLUES_Schema
So now Blue2thprinting https://github.com/darkmentorllc/Blue2thprinting, and other tools that use CLUES, like WHAD https://github.com/whad-team/whad-client, can more easily identify Polara BLE-enabled crosswalks.
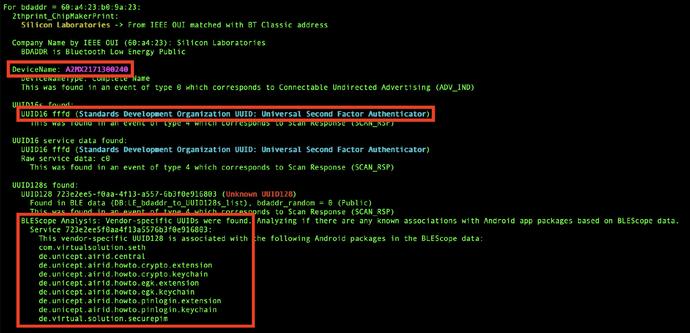
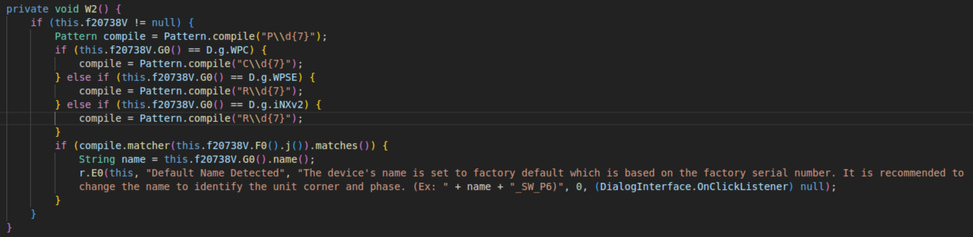
If the assumption is that the devices which were maliciously modified were not reconfigured away from default, then it would be reasonable to assume that devices which still have default names matching the patterns shown in pic2, are more likely to be vulnerable. And of course @WiGLEnet shows plenty of hits for such devices. And indeed, I used WiGLE to go drive to an intersection one county over and confirm that the 4x default-looking devices there were indeed broadcasting the Polara UUIDs (since WiGLE doesn't report the UUIDs, which would be useful for confirmation.)
Thanks to Mike Ryan @mpeg4codec for pointing out a video from Deviant Ollam @deviantollam from last year which made it more obvious what was going on. https://www.youtube.com/watch?v=mvvVSTlbqEI

Bluetooth Low Energy - Full Stack Attack | Veronica & Xeno Kovah | hardwear.io USA 2025
In this training by Veronica Kovah & Xeno Kovah, you will learn how to use fault-injection to do just that. You will learn how to use techniques such as crowbar glitching, spiking and electro-magnetic fault injection to bypass a diverse set of protections, including re-enabling the debug interfaces on microcontrollers, bypassing firmware security measures and recovering AES keys by glitching AES rounds.
From: @xenokovah
https://infosec.exchange/@xenokovah/114055921337012221