Google published a blog post about 0days and the like. This jumped out at me:
Vendor investments in exploit mitigations are having a clear impact on where threat actors are able to find success.
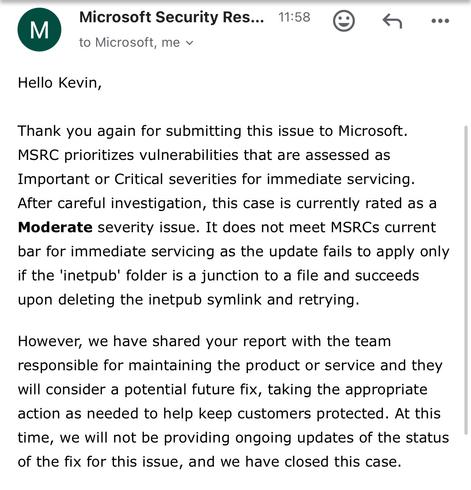
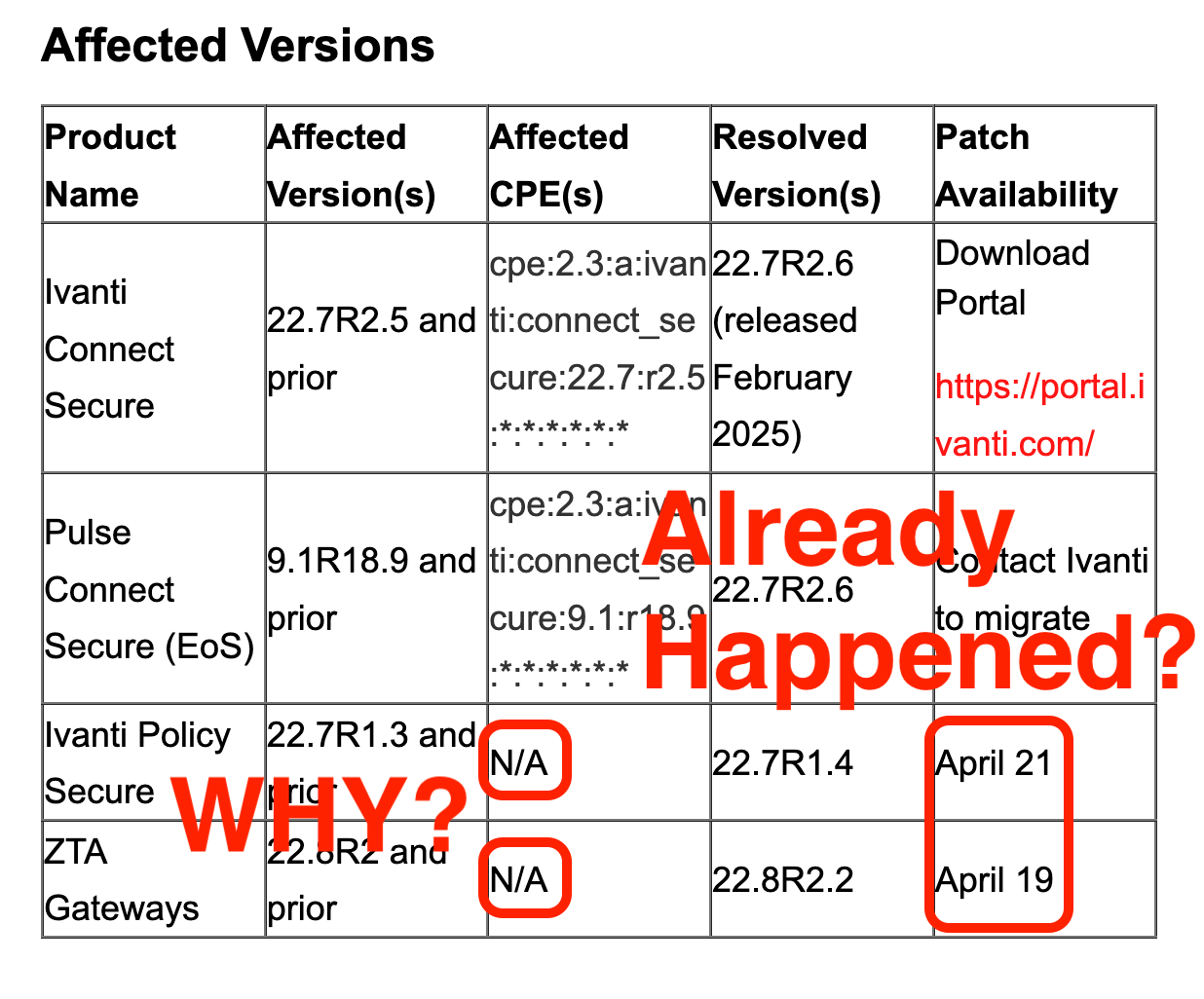
Stack canaries gained popularity in the Linux world in 2002. When did the Linux-based Ivanti ICS product get stack canaries, after years of ITW exploitation? 2025. That's right. They decided to wait TWENTY THREE YEARS before deciding to turn on a compile-time flag that would have prevented successful exploitation of April's CVE-2025-22457.
We all know that comparing the security disposition of companies/products based on CVE counts is both foolish and futile, but sometimes they make it easy for us. 😂