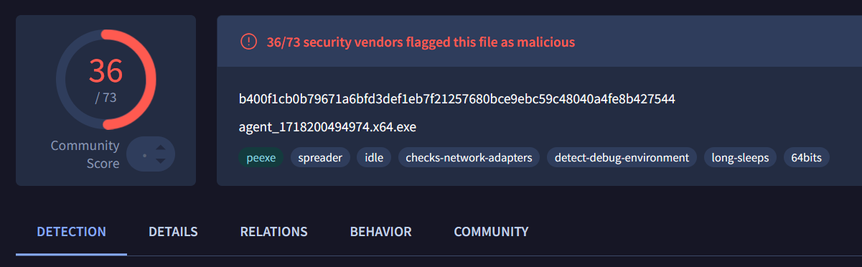
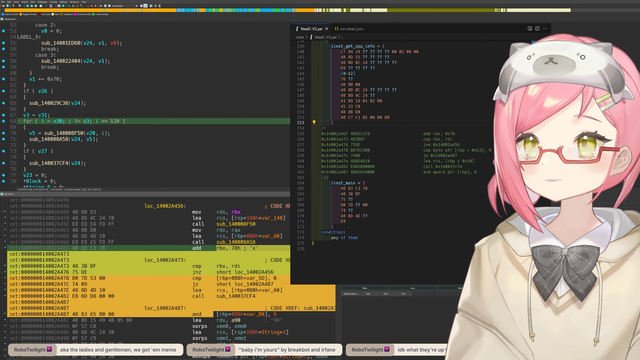
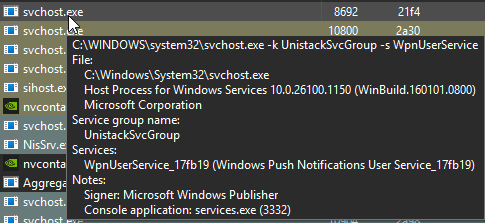
Finally got around to taking a look at StealcV2 today after a few weeks that it's been out
Initial loader (536a64b3267c5056b261d71324793571d02a8714bcb8f395927f72f77d004f56)
-> CF obfuscated shellcode (bdace8aba0dbcac81811d833605fadc157ed95864537d5bf1fc28f125becef1f )
-> Rust-based (1.85.1) loader/injector (f6ce652432d8baf56195c49d34ad89bd7cf933a6af864973f7b03e6bb3acc88e)
-> StealcV2 payload (a26095cf5fff9a7ec04c3fd3fb60372f38f3dc300addf4983e0ce4f7490ef7b2)
Looks like it might have been a major rewrite? I'm not sure I haven't closely compared it against the StealcV1 yet. Strings are Base64 RC4 encoded. The RC4 patterns used in the binary currently causes false negative in capa at the moment - I've filed an issue accordingly.
We also wrote a new YARA rule to detect StealcV2 on stream as well. Surprisingly, my heuristics-based Chromium ABE stealer YARA rule we wrote half a year ago still matches this sample and other known StealcV2 samples.
C2
- 91.92.46[.]133/8f11bd01520293d6.php
Samples, IoCs, and more
https://github.com/Still34/malware-lab/tree/main/reworkshop/2025-04-26
#threathunting #stealc