Effective July 31st, two major Root CAs used by Chunghwa Telecom will no longer be trusted on Chrome 139 and higher. Chunghwa Telecom is the largest telecommunication company responsible for Taiwan's network infrastructure, and their root CA is used to sign certificates used by major Taiwanese government websites.
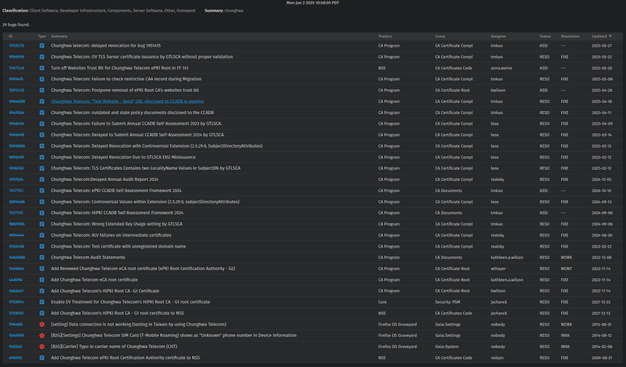
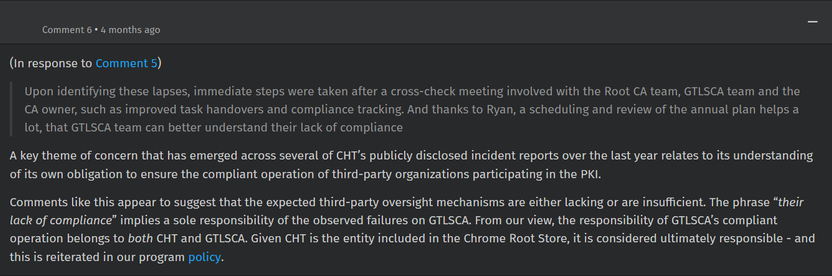
Google cited "compliance failures, unmet improvement commitments and the absence of tangible, measurable progress in response to publicly disclosed incident reports."