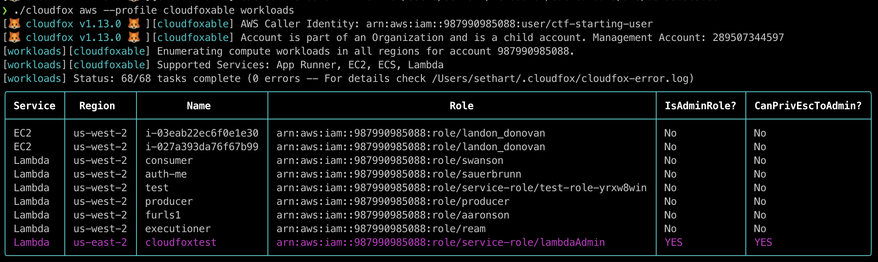
CloudFox v.1.13.0 is out with 2 new AWS commands and a bunch of updates.
* The new workloads command looks at EC2, Lambda, and ECS and highlights any workload that has an admin role attached, as well as any role that can privesc to admin!
* The new api-gws command contributed by Wyatt Dahlenburg finds all API gw endpoints and crafts custom curl commands for you with any API keys found in the endpoint metadata)
* The env-vars command has been upgraded to help you find secrets stored in environment variables. It highlights interesting variable names and creates a separate output file with just the interesting items.
* The role-trusts command has been upgraded to help you find overly permissive role trusts, particularly those that trust :root, without an ExternalID.
https://github.com/BishopFox/cloudfox
#cloudfox #cloudsecurity